Finding Seeds
Basic Flow
Before getting started with Subdomain enumeration, we have to have as much seeds as possible to expand our attack surface.
We can achieve this through:
- Acquisition Recon - Crunchbase
- ASN Enumeration - Hurricane Electric Internet Service
- BuiltWith - Relationship Profile
- Google Dork - Copy right information
Acquisition Recon
WhoisXML
https://tools.whoisxmlapi.com/reverse-whois-search → Not very accurate.
crunchbase
Let’s search up World Health Organization on Crunchbase:
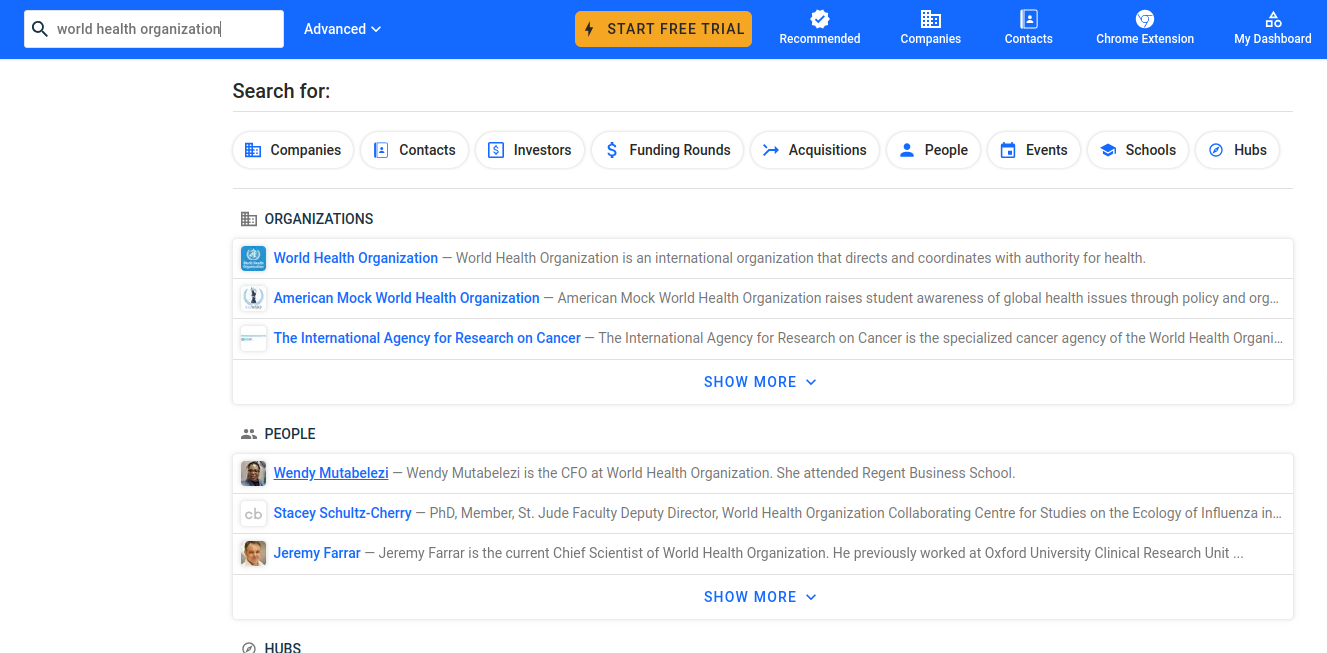
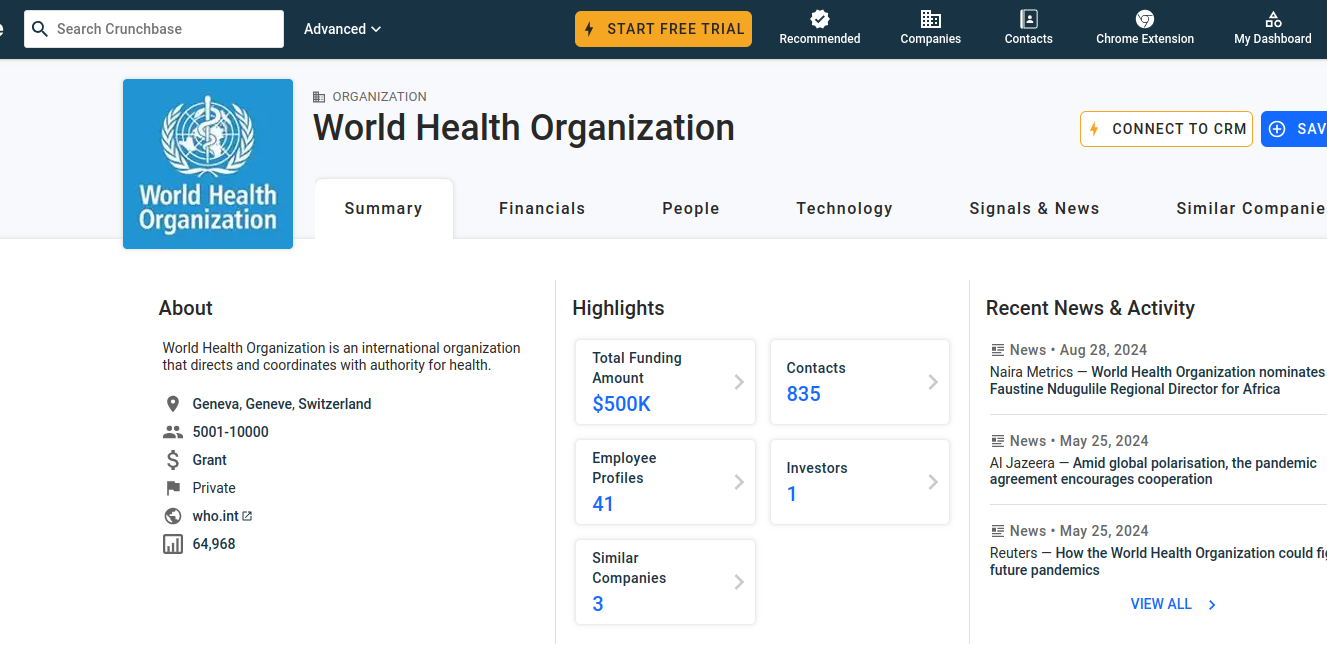
Probably because this is non-profit organization, I don’t see any acquisitions:
For other companies such as Tesla, there is acquisition.
Below, we can see 10 of them:
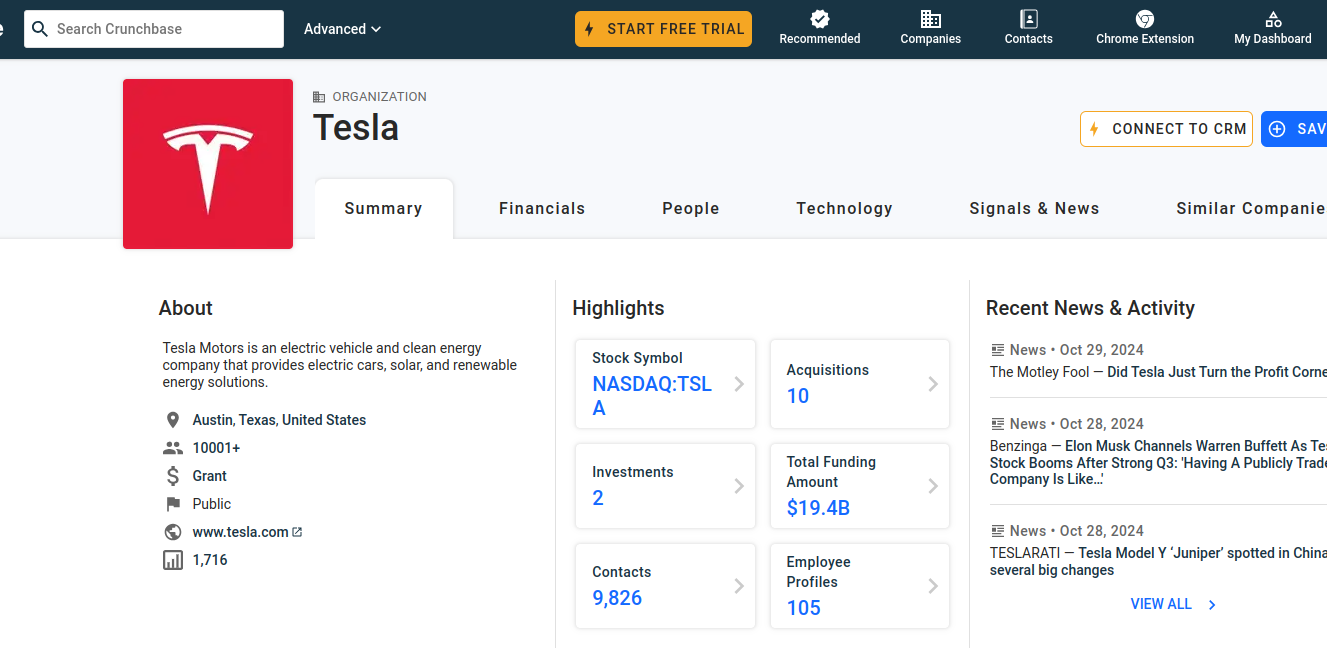
Click on it to list them:
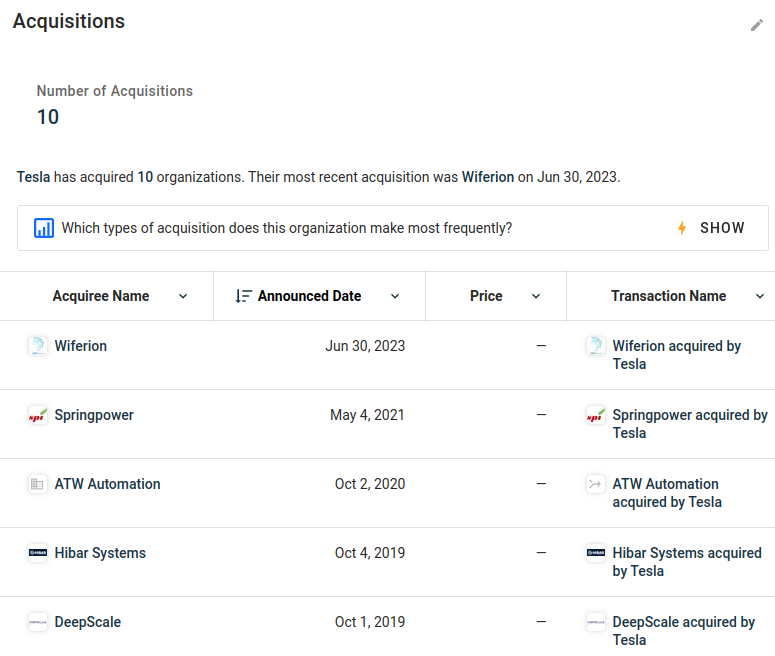
Click on each of the acquisition one by one manually and add them to the scope.
For the example acquisition below, I will be adding www.wifierion.com to the scope:
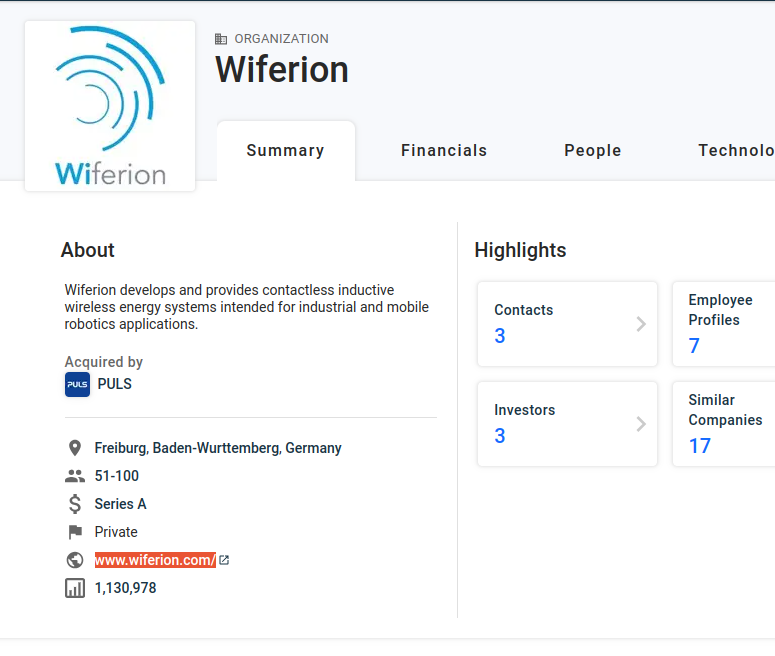
After finishing this step, we should have list of acquisitions ready.
ASN Enumeration
Now let’s move on to ASN enumeration.
Through ASN enumeration, we can obtain scope of IP addresses that belongs to the target.
We will use https://bgp.he.net/ for enumeration.
Our search result shows lot of results and we have to guess which ones should be the correct ones:
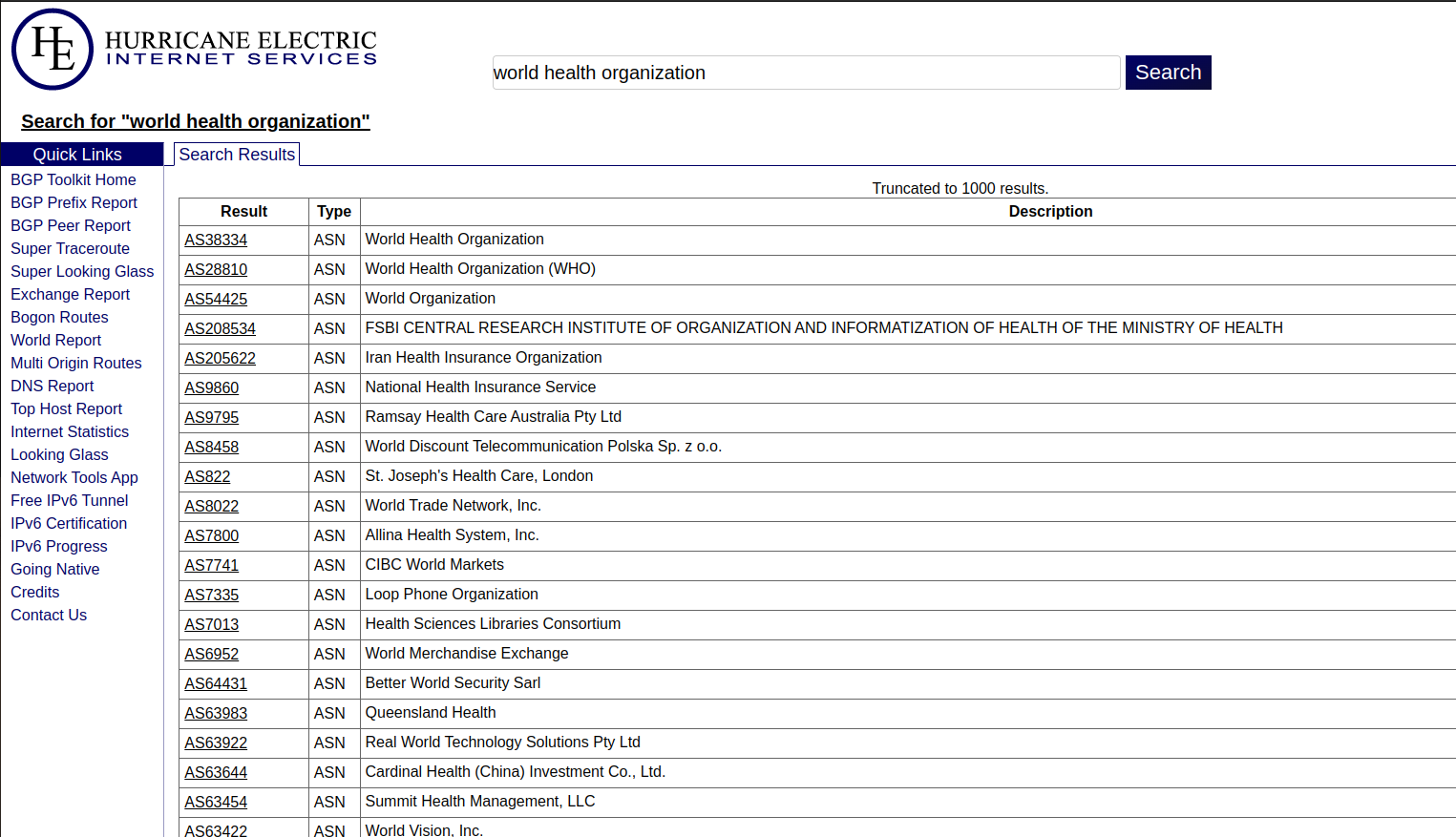
Since AS28810 shows the country as Switzerland, this seems to the correct one. I am not sure about the other ones.
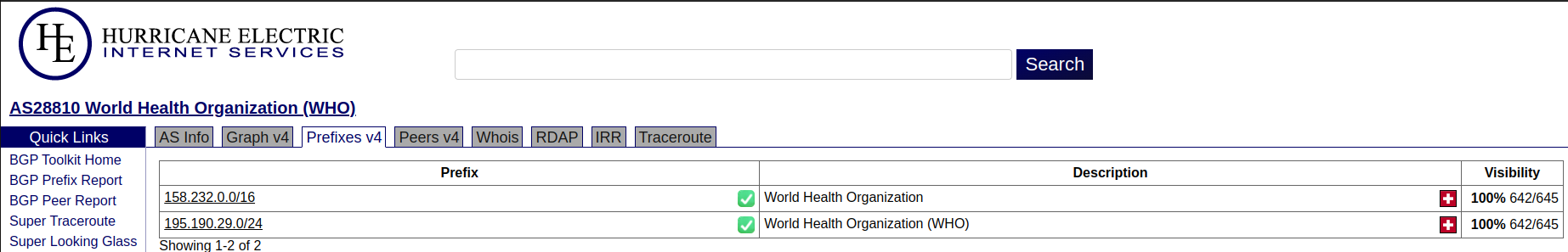
Take a note of the ASN number and the IP address range:
158.232.0.0/16
195.190.29.0/24
Builtwith
Let’s go to builtwith.com and check on companies related to who.int.
Going to Relationship tab, we can see bunch of Google Tags that is being used in who.int:
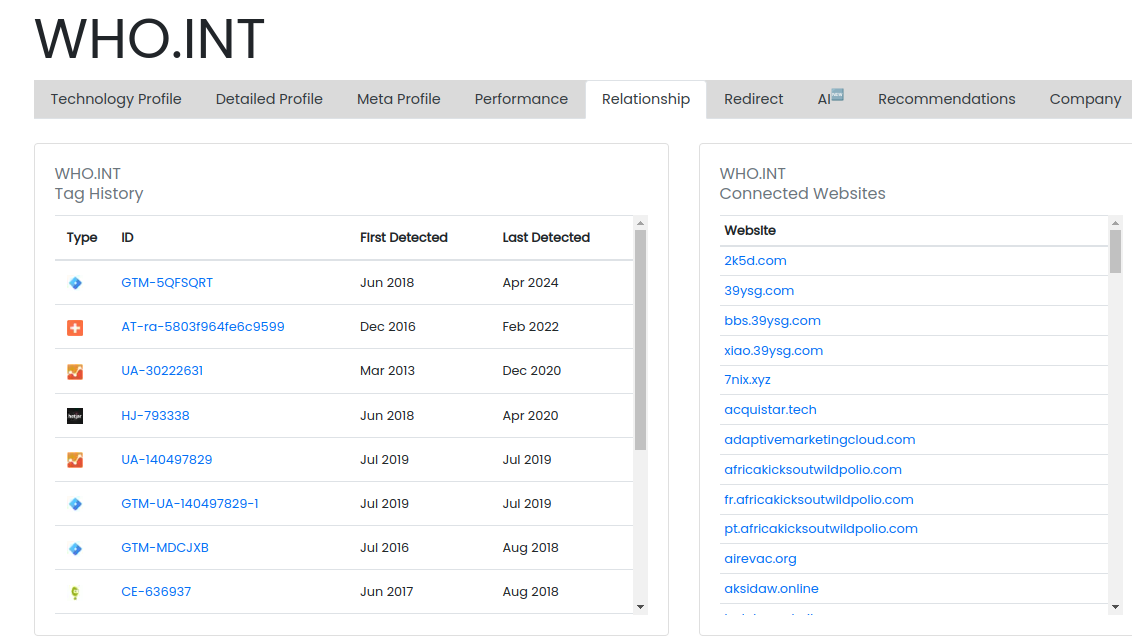
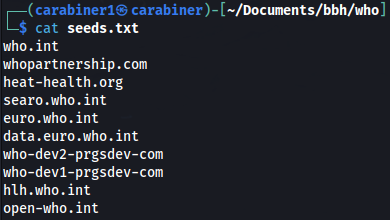
I see some subdomains such as data.euro.who.int on the list.
Take a note on this and add it to the scope since subdomain enumeration might not detect it:
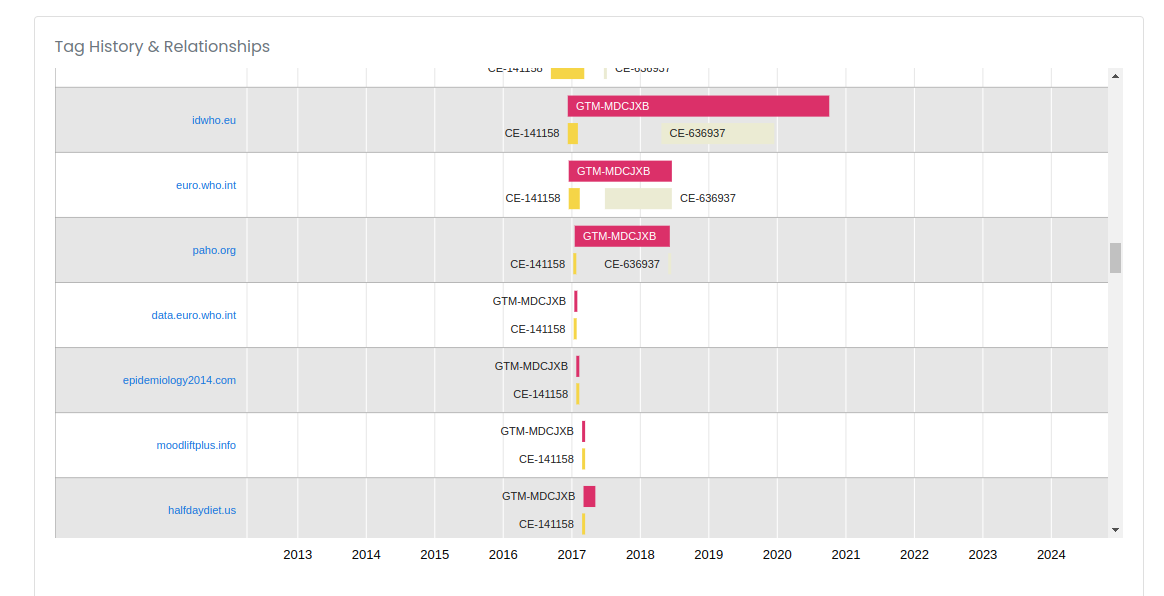
I had a quick check on data.euro.who.int and it got me redirected to cisid.euro.who.int and page seemed juicy at first glance.
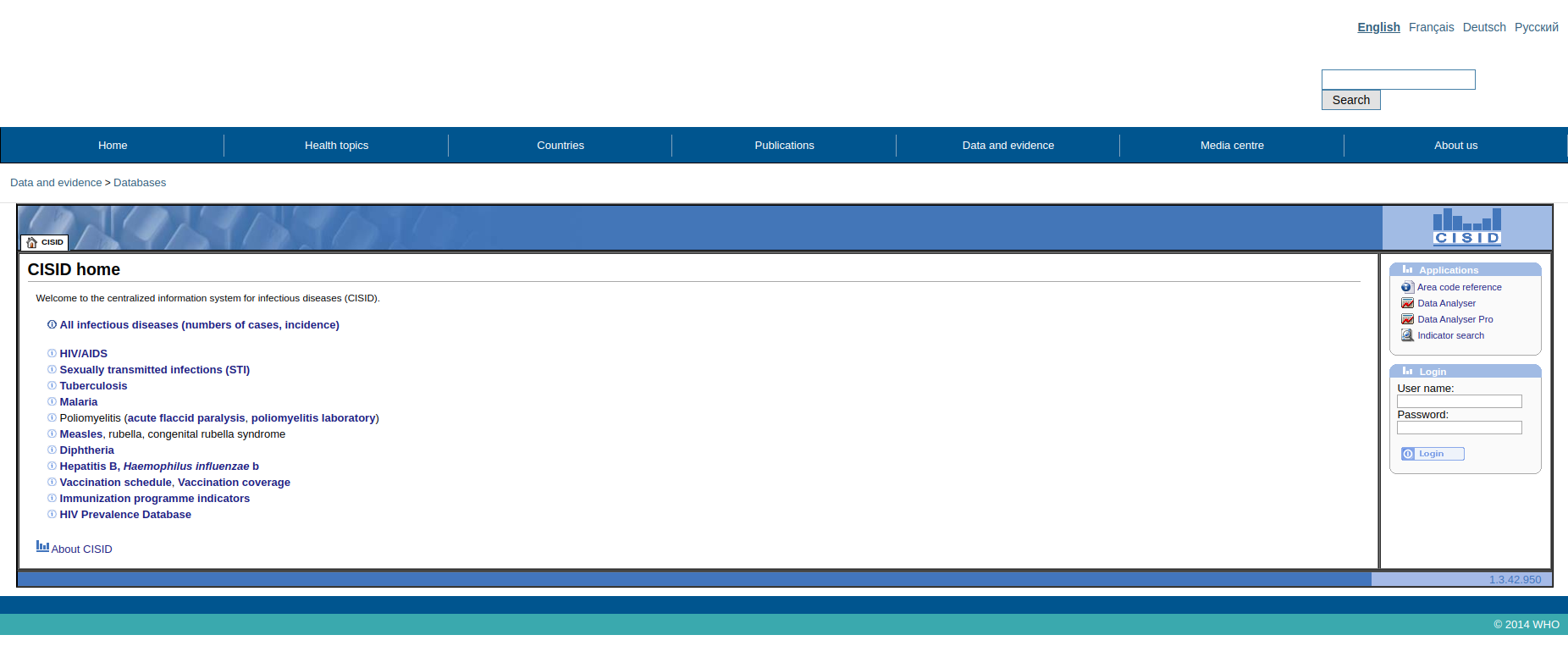
Take note of interesting assets:
https://whopartnership.com/
https://heat-health.org/
http://searo.who.int/
euro.who.int
data.euro.who.int
who-dev2-prgsdev-com
who-dev1-prgsdev-com
https://hlh.who.int/
open-who.int
During my subdomain enumeration, they didn’t catch this subdomain so it proves that we should always check on builtwith.com relationships.
Favicon Hash
What is favicon hash?
favicon hash is a unique identifier generated from the favicon of a website. It is used to represent a website and usually displayed in the browser’s address bar or tab.
Find Favicon
When visiting the target website, open developer tool and go to network tab.
favicon.ico should be there.
e.g
https://s.yimg.com/rz/l/favicon.ico
Copy the URL for later use.
Calculate Favicon Hash
Use the script below to calculate the favicon hash:
import mmh3
import requests
import codecs
response = requests.get('https://in.search.yahoo.com/favicon.ico')
favicon = codecs.encode(response.content,"base64")
hash = mmh3.hash(favicon)
print(hash)Above script will give result such as 1623284567
Search Asset
Shodan
On Shodan, search for the hash:
http.favicon.hash:1523284567
Click on any of the IP in the result and we will be able to see all subdomains and ASNs.
Check all the IPs one by one and hope on finding some of the hidden subdomains, IPs, and ports.
Now let’s copy all the discovered assets and run nuclei on it.
To copy results from shodan as a text:
- Click on more on the right corner down:
![]()
- Choose IP:
![]()
- Copy
![]()
Automation
Tools that will help with finding favicon and find assets:
These scripts will help you find favicon hashes which you can use in shodan to widened your attack surface
- https://github.com/Mr-P-D/Favicon-Hash-For-Shodan.io
- https://github.com/devanshbatham/FavFreak
- https://github.com/edoardottt/favirecon
- https://github.com/eremit4/favihunter
Google Dork
CopyRight
Lastly, do Copyright dorking on Google as such:
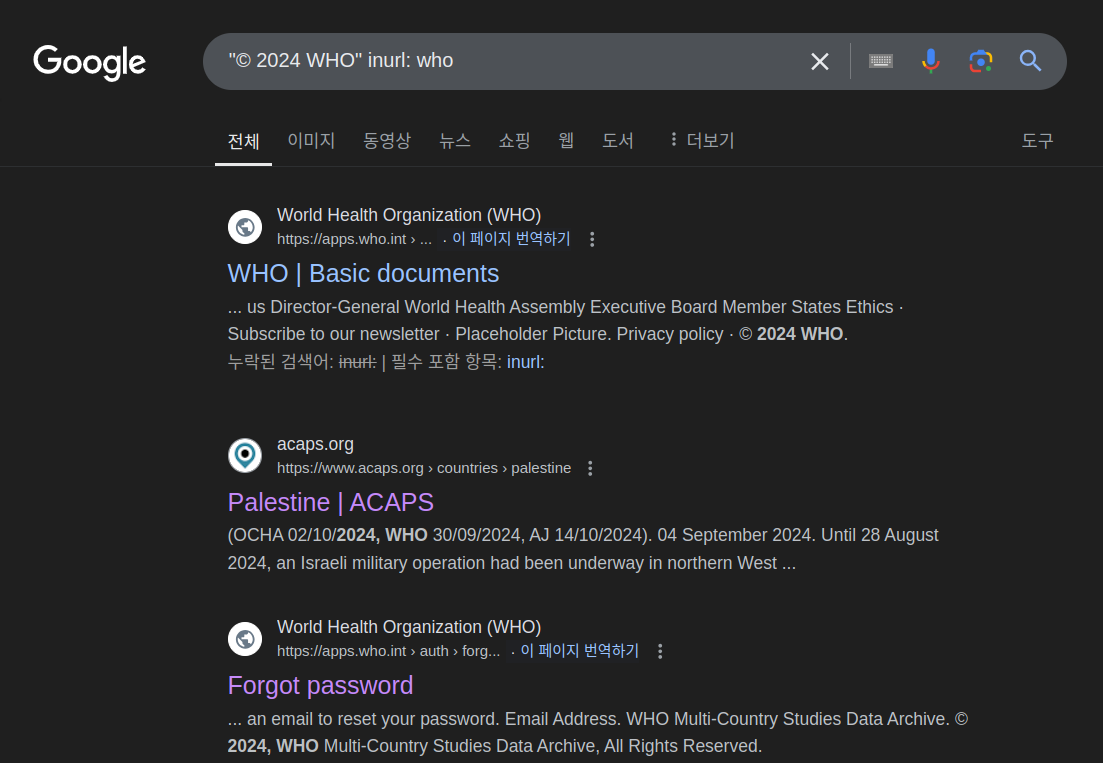
It didn’t find nothing new, but it did found some juicy webpages as below:
https://apps.who.int/healthinfo/systems/surveydata/index.php/auth/forgot_password
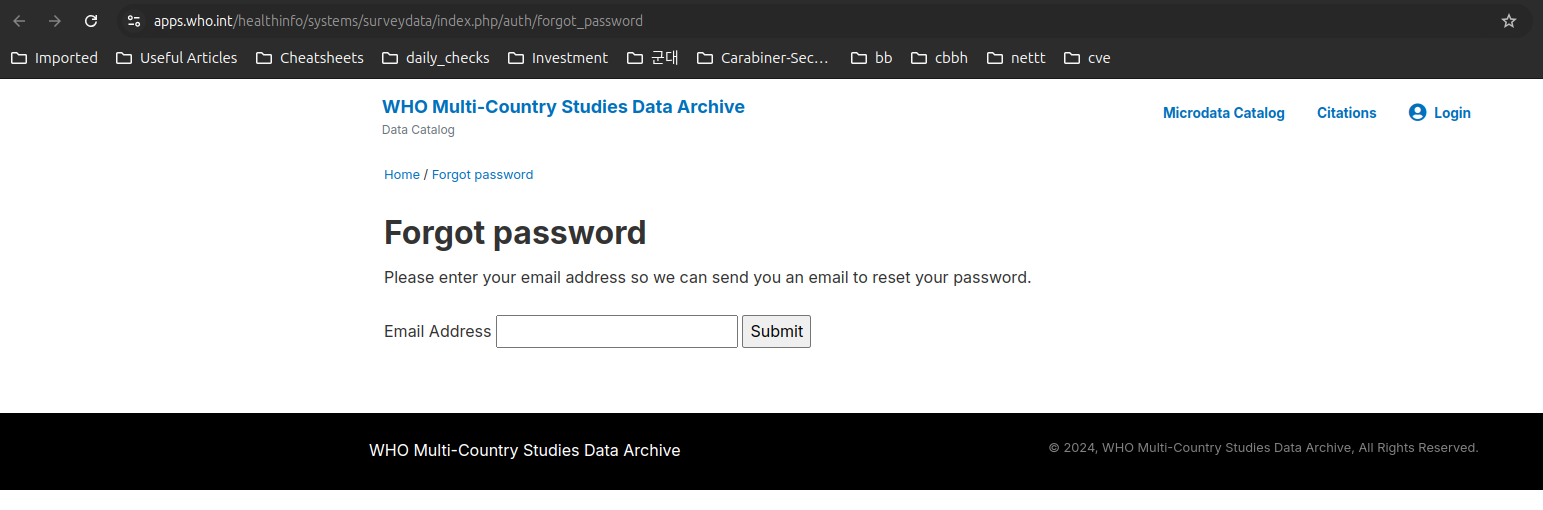
Result
On seeds.txt, I saved all the seeds discovered from who.int: